What is EternalBlue?
EternalBlue is a Microsoft software exploit developed by the NSA (National Security Agency) to gather intelligence — the exploit allows remote access to data on Microsoft devices. EternalBlue was stolen from the NSA in 2017 by the hacker group Shadow Brokers, and it has since been used to launch devastating cyberattacks around the world such as WannaCry, Petya/NotPetya, and Indexsinas.
How does EternalBlue work?
The EternalBlue exploit (also known as MS17-010) takes advantage of a flaw in a network file-sharing protocol in Microsoft computers called SMBv1. The Server Message Block version 1 network protocol helps computers share files with printers, ports, and other Windows machines. But SMBv1 contains bugs that let hackers send malicious data packets into the network. Once inside, malware can spread to all of the devices on the network and beyond.
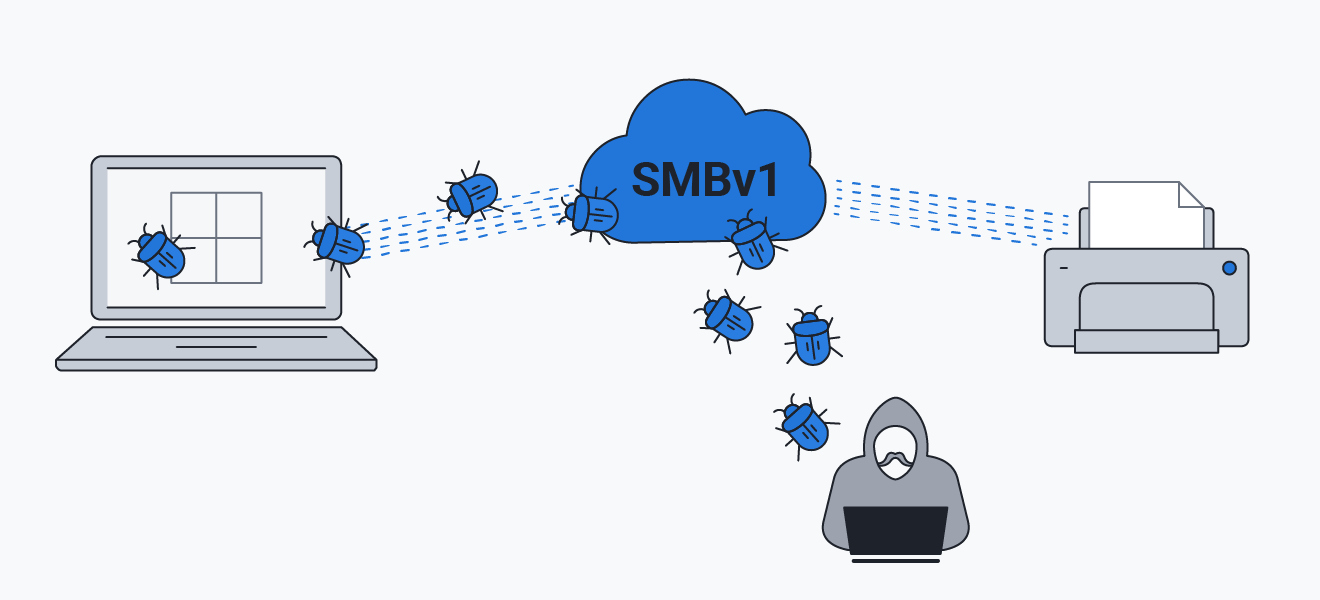 EternalBlue takes advantage of SMBv1 vulnerabilities.
EternalBlue takes advantage of SMBv1 vulnerabilities.
Despite Microsoft’s attempts to fix the vulnerability and protect users, hackers used this computer exploit to launch some of the largest cyberattacks in history. Today, most Microsoft machines are protected against EternalBlue, but many are still at risk.
If EternalBlue is old, why should we worry?
The most infamous cyberattacks involving the EternalBlue exploit occurred in 2017. Since then, most Microsoft devices have been patched — meaning the EternalBlue vulnerability has been fixed. But there are still many devices that haven’t received the vital security patch.
The software update that fixes EternalBlue’s vulnerabilities and exposures (named the MS17-010 patch) has one weakness: it needs to be installed by the user. Researchers have estimated that there are over 1 million SMB servers accessible to anyone on the internet, and many are vulnerable to EternalBlue attacks.
Indexsinas
Indexsinas is the latest EternalBlue attack to go global. Indexsinas is a computer worm, which is a self-replicating computer virus that infects one computer, replicates, then infects another. Worm attacks cause a chain reaction of infection that’s difficult to stop.
Since 2019, Indexsinas has been gaining access to Windows servers using the EternalBlue vulnerability. Once a device is infected by the worm, attackers can use it however they like. They can delete files, control functions, and even sell access to your computer to other malicious actors and dangerous hackers. It is believed that computers affected by Indexsinas are being used to mine cryptocurrency, which is then deposited into the wallets of the attackers.
Indexsinas is alive and well, and it’s possible the hackers behind it won’t be caught anytime soon. To stay protected, individuals and businesses using Microsoft devices should perform regular updates to patch vulnerabilities. With powerful antivirus software like AVG AntiVirus, you can run a network scan to see if your device is vulnerable to EternalBlue or other security vulnerabilities.
EternalBlue history: years of data havoc
EternalBlue is a bit like Frankenstein’s monster. It was purposefully created by the US government, who then lost control over it. Since then, it’s roamed the world causing havoc wherever it goes — and it just won’t die.
Exactly when the EternalBlue exploit was identified is unknown, but we know that it was originally found by the US National Security Agency (NSA) as a part of its plan to stockpile and weaponize cybersecurity vulnerabilities. Apparently, the NSA used EternalBlue for years to gather intelligence.
Then, in April 2017, the NSA was hacked by the hacker group Shadow Brokers, and EternalBlue was exposed. Shadow Brokers leaked EternalBlue on Twitter (now X), unleashing it into the world. EternalBlue is logged in the National Vulnerability Database as CVE-2017-0144.
About a month before the leak, Microsoft had released Security Bulletin MS17-010 — a patch for the EternalBlue exploit. This suggests that the NSA likely informed Microsoft of the breach shortly after the Shadow Brokers hack. But Microsoft’s efforts weren’t enough to stop major cyberattacks that began just one month after the Shadow Brokers’ leak. Millions of individuals and organizations were vulnerable to data theft and a whole gamut of malware.
The biggest hacks made possible by EternalBlue were WannaCry and NotPetya, both of which began within two months of the EternalBlue leak.
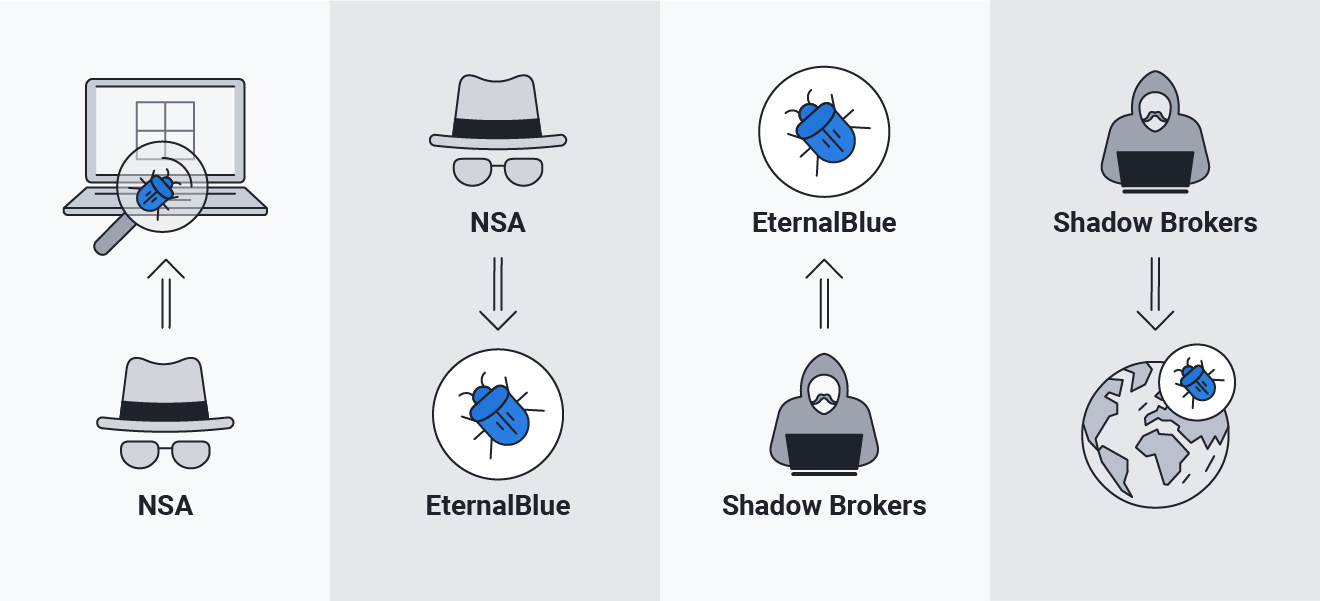 EternalBlue was discovered by the NSA and was later spread by the hacker group Shadow Brokers.
EternalBlue was discovered by the NSA and was later spread by the hacker group Shadow Brokers.
WannaCry
WannaCry was the first major cyberattack that took advantage of the EternalBlue exploit. Unleashed in May 2017, about a month after Shadow Brokers leaked EternalBlue, WannaCry was a type of ransomware attack, which is a cyberattack that captures data and locks it behind a paywall until a ransom is paid.
Spreading quickly, WannaCry didn’t have a specific target, but it wasn’t long before major institutions were affected. Some of the biggest names included FedEx, LATAM Airlines, and the UK National Health Service (NHS). The damage caused by WannaCry is estimated to be in the billions of dollars.
Petya/NotPetya
Petya was a cyberattack that was originally launched in 2016. But at the time, it didn’t do much damage. EternalBlue was the tool it needed to become a truly devastating attack. About a month after WannaCry, the second version of Petya (named NotPetya), began to spread by targeting the EternalBlue vulnerability.
NotPetya was a ransomware attack with a particularly insidious twist: It was a virus without a cure. It permanently encrypted a computer’s Master File Table (MFT) and Master Boot Record (MBR). Even if you paid, your files would not be released — systems affected by NotPetya were disabled for life.
WannaCry had only just made headlines as one of the biggest hacks in history. Now, just a month later, NotPetya dwarfed WannaCry in its reach and the cost of the damage it caused.
The staggering cost of EternalBlue
It’s difficult to determine the cost of EternalBlue’s global havoc, especially because it continues to cause damage to this day.
WannaCry and NotPetya are each estimated to have caused billions of dollars in damage, with NotPetya the worst offender. And ongoing Indexsinas is still racking up its bill.
Here are some of the organizations that have seen the largest losses due to EternalBlue:
When you add up the numbers, it’s easy to see why EternalBlue is still such a big deal today. Hackers continue to use this exploit to wreak havoc, and they won’t stop until they can no longer do so. Every Microsoft device should be protected by the best free antivirus software possible to help prevent EternalBlue and block other dangerous threats.
How to fight off EternalBlue attacks
EternalBlue is like an unlocked backdoor to your computer, giving hackers access to your personal data or even your entire network. Hackers can easily enter and deposit any malware they like, from ransomware to worms to trojans and more.
Here’s how to prevent EternalBlue attacks and potentially being hacked:
Keep your devices updated
Whether you’re an individual or running a business, ensure that all of your Microsoft devices are updated. Updating your devices will automatically install the EternalBlue patch MS17-010, effectively closing the door that EternalBlue left open.
-
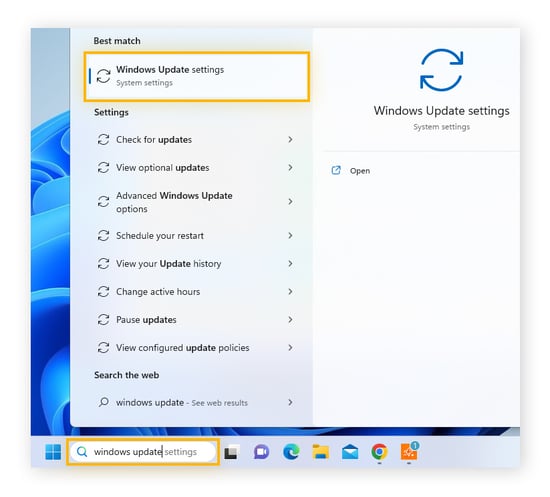
Start typing Windows Update settings into the search box, then click Open.
-
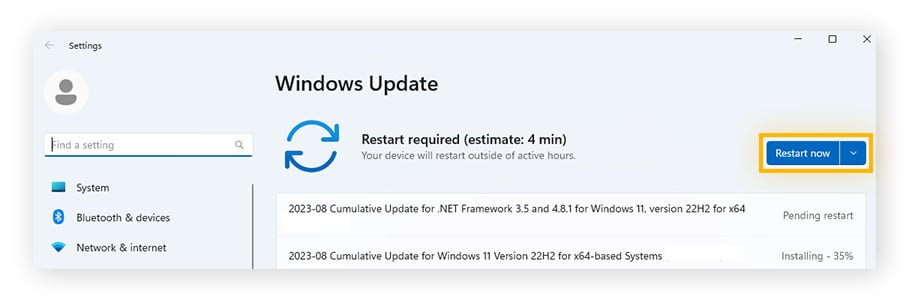
Click Restart now if there are updates available or Check for updates.
Disable SMBv1
SMBv1 is the buggy protection protocol that causes the EternalBlue vulnerabilities. Disable it if it’s on your PC — typically, it’s on older versions of Windows.
SMBv1 isn’t installed by default in:
You can disable SMBv1 through PowerShell:
-
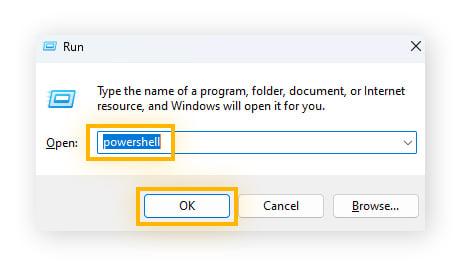
Open PowerShell by pressing the Windows + R keys, then type powershell, and click OK.
-
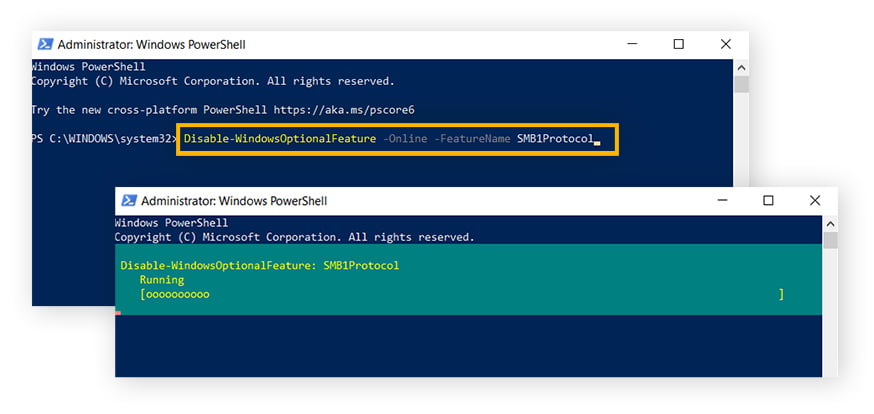
Enter the command Disable-WindowsOptionalFeature -Online -FeatureName SMB1Protocol and hit Enter.
Download antivirus software
It’s critical to install reputable antivirus software onto all of your devices. This will protect you from EternalBlue and help prevent other hacking and malware attacks.
To install our free antivirus software, follow these steps:
-
Download AVG AntiVirus.
-
Follow the on-screen instructions to open AVG AntiVirus and install it.
Install EDR software (for businesses)
If you’re running a business, ensure that every device on your network has efficient endpoint detection and response (EDR) software. This technology protects against cyberattacks and detects suspicious behavior and potential threats on devices to fight them before they can do damage.
Protect yourself against online threats with AVG
The digital world is full of threats, and cybersecurity attacks wreak havoc on businesses and individuals all the time. But by taking the right precautions, you can help protect yourself from cyberattacks and malware.
AVG AntiVirus helps block unsafe links, prevent computer viruses, and identify vulnerabilities like the EternalBlue exploit to help safeguard your digital life. Get industry-leading online protection today.

 EternalBlue takes advantage of SMBv1 vulnerabilities.
EternalBlue takes advantage of SMBv1 vulnerabilities. EternalBlue was discovered by the NSA and was later spread by the hacker group Shadow Brokers.
EternalBlue was discovered by the NSA and was later spread by the hacker group Shadow Brokers.








