The dark web is widely used to protect users’ anonymity online and help people access crucial content — such as journalism and enforcement agency reporting pathways — more securely and without fear of reprisals. However, it can still be a dangerous place if you’re not careful.
6 steps to get on the dark web
The easiest way to access the dark web is with the Tor browser. However, depending on your goals and overall system security, Tor alone may not be enough to fully protect your privacy.
In this guide, we explain a technique known as Tor-over-VPN, which routes your traffic through a VPN before it reaches the Tor network. This setup helps obscure your IP address from your internet service provider (ISP) and hides your Tor use. With Tor-over-VPN, your ISP will only see that you’re connected to the internet with a VPN, not with Tor.
We’ll also provide tips on navigating the risks associated with the dark web, such as illegal material and increased malware exposure.
1. Prepare for accessing the dark web
Making a plan for your dark web session and plugging potential gaps in your cybersecurity can help maintain your anonymity and avoid malicious content. It helps to know what you’re looking for and install the relevant privacy and security tools ahead of time.
Here’s what to do before you connect to the dark web:
Define your goal
Unlike the surface web, you can’t browse the dark web using traditional search engines like Google or Bing. Alternative dark web search engines exist, but they’re often incomplete — dark web sites can’t be crawled and indexed like on the surface web — and could expose you to malicious or illegal content.
The safest way to navigate the dark web is to know what you want to look for ahead of time. We recommend sourcing a list of reputable .onion sites and navigating directly to the URL. For extra security, you may want to first install the Tails operating system, too.
Connect first through a no-log VPN
Many people use the dark web to access information freely, without fear of tracking or censorship, and to preserve their privacy. If you’re this way inclined, you may also want to use a VPN.

Important:
Using a no-log VPN for a Tor-over-VPN connection is key. This means that the VPN provider you use doesn’t store records of browsing activity, connection data, or IP address. If you use a VPN that keeps logs, the privacy benefits of using the Tor-over-VPN protocol are basically nullified, as the VPN provider can trace your activity logs, even if your ISP can’t.
Among the many benefits of using a VPN is that a trusted, no-log VPN can enhance your privacy when used with Tor, a setup known as Tor-over-VPN. While Tor protects your browser traffic, a VPN shields the rest of your network activity, like email apps, background refreshes, and system updates. It also encrypts your connection to Tor’s entry node, preventing your ISP from seeing that you’re using Tor at all.
So not only is your web activity hidden by Tor, but you can also mask your IP address for other network processes by connecting via a range of global VPN server locations.
Close all open apps
Closing all apps before browsing privacy-sensitive areas of the internet reduces the chances your system will leak data or expose you to malware and identity theft. Open programs can log, sync, or share information in the background, reveal your real IP address, or create data traces that undermine your anonymity. Closing them limits what your system broadcasts and makes your session harder to correlate with your identity.
Install Tor Browser
Tor Browser is the standard browser used for accessing the dark web — it’s quick and easy to install via the official Tor Project website.
To download and set up Tor Browser:
-
Go to the Tor browser download page and select your operating system (macOS, Windows, Linux, or Android) from the list of available downloads.
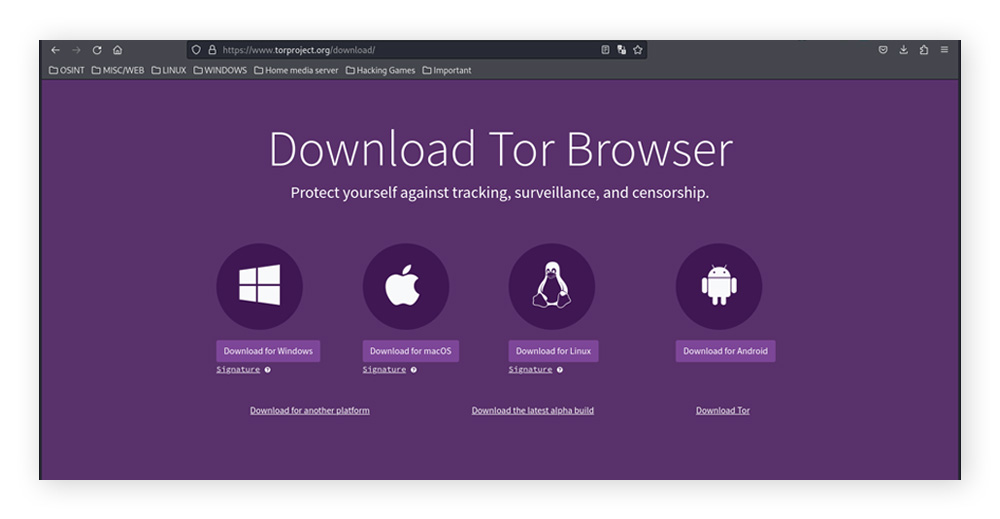
-
If possible, verify the file signature before running the installer. These tools check that the .exe file was created by the Tor Project and hasn’t been changed. To do this, use a trusted verification tool like Gpg4win on Windows or GPGTools on macOS.
-
To check the file signature, save the .asc signature file from the download page into the same folder as the .exe file. Copy the Tor Project’s public key, then open your verification tool and click Import Key (or similar) and run the check. If the tool reports Good signature from Tor Browser Developers, the file is safe to install. Do not continue if it reports BAD signature or No public key.
-
Now, you’re free to run the .exe file as an administrator and follow the prompts to finish the installation.
If you intend to browse the dark web on your Android phone, you can install the Tor Browser app directly from Google Play.
Tor Browser isn’t available on iPhones due to Apple’s App Store restrictions. Apple requires all iOS web browsers to use its WebKit rendering engine, which Tor Browser does not. If you have a jailbroken iPhone, you might find Tor-related APKs in third-party app repositories, but installing them is risky — they aren’t verified by the Tor Project or protected by Apple’s security controls. We don’t recommend jailbreaking your phone or installing apps from third-party sources.
Tor Browser isn’t available on iPhones due to Apple’s App Store rules. Apple requires all iOS browsers to use its WebKit rendering engine, which Tor Browser doesn’t support. If you have a jailbroken iPhone, you may see Tor-related apps in third-party repositories, but installing them is unsafe — they aren’t verified by the Tor Project and aren’t protected by Apple’s security controls. Avoid jailbreaking your device or installing apps from untrusted sources.
The Tor Project recommends that iPhone users install Onion Browser — you can download the app directly from the App Store. Although Onion Browser helps route your traffic through Tor on iOS, it may not match Tor Browser’s protections on its official apps.

2. Enter the dark web
To access the dark web, connect to your VPN and then open Tor Browser. Make sure you wait for your VPN to fully establish and for the browser to finish loading before you take the next step. This ensures that your traffic is routed through the secure tunnel and your real IP address isn’t exposed.
-
On Windows, Linux, or macOS: Turn your VPN on > Open Tor Browser > Click Connect.
-
On Android: Turn your VPN on > Open the Tor Browser app > Tap Connect.
-
On iPhone: Turn your VPN on > Open the Onion Browser app > Tap Connect to Tor.
3. Perform an IP leak check
Before you start browsing any dark web sites, perform a simple IP leak test to check your connection is truly private.
Go to a reputable IP/DNS leak test website (we recommend ipleak.net or doileak.com) using the Tor browser to check your IP address and location. If the result matches your real location, or if you see multiple IP addresses displayed, your VPN is not working properly and your anonymity is at risk.
To troubleshoot, close the Tor browser and disconnect your VPN. Check that your VPN is set up correctly, turn it on, and test again. Once your IP leak check shows you’re properly encrypted, you’re ready to explore the dark web.
4. Surf dark web domains
To get started surfing the dark web, pull up your list of .onion sites to visit and paste them into the navigation bar, one at a time.
Common starting points for people new to the dark web include:
-
The Hidden Wiki — a directory with links to dark web websites. Some sites that haven’t been thoroughly vetted may contain malware or host illegal content or activities, so always exercise caution.
-
Facebook’s onion address — an official hidden version of its site on the dark web, and allows privacy-conscious users to access the site through Tor without losing cryptographic protections.
-
The CIA’s onion address — officially launched in 2019, allowing dark web informants to supply them with information without fear of being compromised.
-
.onion versions of major news websites — The New York Times, BBC News, CNN, Al Jazeera, and Bloomberg all have official onion addresses. These sites can be vital resources for people living in countries with limited press freedoms.
.onion URL structure
You may notice that dark web sites have an unusual URL structure. Each .onion address is generated from the service’s public cryptographic key and consists of a 56-character string of numbers and lowercase letters, followed by the top-level domain “.onion”.
For example: q3z5l2b1n0k7c9v4m8y2p6s0t3u5w7x9a2b4c6d8e0f1g2h3i.onion
This creates a highly secure and anonymized web address that protects both users and site owners. Earlier versions of .onion sites contained 16, rather than 56, characters. However, these are now defunct.
5. Find dark web content
In addition to visiting specific .onion sites you researched, you can also browse the dark web with a dedicated dark web search engine. Well-known dark web search engines include:
-
Ahmia
-
Torch
-
Haystak
-
OnionLand

Important:
Many online sources list DuckDuckGo as a dark web search engine. But while there is an .onion version of DuckDuckGo, it only provides clearnet results, i.e., it does not provide dark web sites in the search results. Using DuckDuckGo on the dark web is best for clearnet users who want extra privacy, but aren’t looking for dark web results.
Regardless of which dark web search engine you use, it’s extremely important to exercise caution when using a dark web search engine. Many of them are uncensored, indexing sites with both legal and illegal content or activities. This means you run the risk of encountering unlawful content, which can get you in serious trouble with the authorities, or becoming the victim of malware, fraud, or hacking.
Dark web search engines work differently to surface web varieties, like Google. The dark web cannot rely solely on crawling in the same way the surface web is — indexes are sometimes added to dark web search engines manually by the site operator, too.
6. Exit the dark web session
To end a dark web session safely, fully quit the Tor Browser — make sure it closes completely rather than running in the background. You can disconnect your VPN afterward if you choose, though this isn’t required to conclude the session. Once Tor is closed, you can resume using your device as usual.
If you’re concerned about malware you may have picked up while surfing the dark web, you can use antivirus software to scan for and remove anything suspicious.
How do I stay safe on the dark web?
Staying safe on the unregulated dark web requires some vigilance. Its seedy reputation, fostered by controversy like that surrounding the Silk Road website, is well-earned. As well as attracting cybercriminals, who use the anonymity it provides to offer hacking and phishing services, the dark web is awash with illicit forums, malware, and other potentially dangerous content.
While the dark web is used for several noble pursuits as well, it’s good to stay on top of these safety practices during a session:
-
Use Tor-over-VPN: Pairing Tor with a VPN keeps your ISP from easily finding out you’re accessing the dark web, and it makes it harder for anyone to tie Tor usage to you.
-
Ensure Tor is up to date: Regularly update your Tor Browser app to benefit from security patches and enhancements. Using updated software helps mitigate risks and protect you against cybercriminals exploiting security vulnerabilities.
-
Disable JavaScript: JavaScript is a code used on most surface web sites to run complex functions and display intricate templates. But it can allow you to be tracked more easily and open up other attack vulnerabilities. Many dark web sites look outdated and basic because they expect their users to have JavaScript disabled.
-
Don't share personal information: One of the big reasons the Tor network exists is for individuals to remain anonymous while browsing. Don't provide any personal information that could be used to expose your identity.
-
Stay away from anything that looks illegal: It’s easier to stumble across illegal content on the dark web than on the surface web, even if this isn’t your intention. If you’re ever unsure, avoid visiting a site or clicking a link.
-
Use anti-malware tools: Use a strong antivirus like AVG AntiVirus Free to run regular malware scans to help keep your system healthy and combat other online threats.
-
Avoid downloading files: Malware can easily be hidden in innocent-looking files, and if it gets downloaded and executed, you could find yourself with ransomware or a keylogger infecting your system.
-
Make purchases with cryptocurrency: Buying items and services on the dark web can be risky (or even illegal). If you do make a lawful purchase, use Bitcoin or another cryptocurrency — never enter your credit card or banking details. Most websites won't even have the option to pay via credit card, and if they do, they’re likely a scam aiming to collect your payment details for fraud.
-
Cover your webcam: Keep your webcam covered and reinforce this with cybersecurity software, which can help stop untrusted apps from using your webcam to spy on you or carry out other scams.
Risks of accessing the dark web
The two main risks of accessing the dark web are engaging with illegal material and being exposed to malware.
The dark web hosts a number of marketplaces that house illegal activity, such as drug and firearms sales, terrorism, hacking services, identity theft, illegal pornography, and even human trafficking. It’s estimated that 60% of sites on the dark web are involved in some form of illegal activity.
Law enforcement and intelligence agencies worldwide monitor the dark web to identify and apprehend criminals. While simply browsing the dark web isn’t illegal in the United States, visiting illicit marketplaces and forums, even by accident, puts you at risk of surveillance and potential legal risks if you engage with illegal material.
The perceived freedom of the dark web also makes it a potential hotbed for cyberattacks. Clicking on the wrong link or downloading files on the dark web exposes you to the risk of ransomware, spyware, phishing scams, and data breaches.
The best way to avoid these risks is to avoid browsing the dark web at random — only visit official onion websites via URLs you’ve acquired through a trusted source.
Use a VPN to stay safer on the dark web
If you want to access the dark web, your first step toward a more private experience should be to secure your internet connection and data with a reliable VPN.
AVG Secure VPN scrambles all your internet traffic and routes it through secure servers to help keep your location and identity hidden. It uses military-grade data encryption to help mask your online activity and keep the data you send and receive more private. Start your free trial now and boost your browsing privacy today.









%20-%20refresh/Signal-What-is-streaming-Thumb-refresh.jpg)







