What is social engineering?
We can define social engineering as a psychological attack that exploits human behavior or our cognitive biases. It usually involves tricking people into unknowingly divulging sensitive information that can be used for corrupt or criminal purposes. Hackers use social engineering techniques to extract personal information they can use for identity theft or other frauds or crimes.
At a time when people are growing increasingly savvy online, social engineering requires some finesse. It’s often a multi-step plan to first gain trust and then access the targeted information.
Unlike cybersecurity attacks that exploit the structures of software and computer code, social engineering attacks rely on the fact that humans err and can be manipulated. Social engineering attacks often target sensitive information like login credentials, social security numbers, bank details, or other personal information.
How does social engineering work, exactly?
Social engineering scams can happen during in-person interactions and over the phone, but often they occur online. In fact, social engineering underpins a wide variety of cyberattacks, because it’s easier to pull off online.
In the physical world, we’re able to assess our interactions with people based on information we receive through our senses. Observing someone’s mannerisms and listening to their tone of voice gives us clues about whether something is fishy or not.
When we’re online, we’re often interacting with faceless companies that process our payments and send our messages. That means we have to rely on familiar graphics or branding and a recognizable pattern of clicks and confirmations to signal that everything seems normal.
Social engineering tactics usually work as a cycle:
-
First, an attacker gathers background information — also known as profiling — and chooses a point of entry.
-
Next, the attacker initiates contact and establishes a connection.
-
Once the connection is made and the attacker is perceived as a trusted source, the attacker exploits the target.
-
After the sensitive information is gained, the attacker disengages and disappears.

Social engineering attacks exploit people’s trust.
To complete the cycle, attackers usually employ social engineering techniques, like engaging and heightening your emotions. When your emotions are running high, you’re less likely to think logically and more likely to be manipulated.
Let’s look at a classic social engineering example. Bad actors could get a list of people who gamble online. They assume that these people will respond to a message that arouses curiosity, excitement, urgency, or fear. The attackers impersonate a lottery company, imitating its font, logo, and colors. The message congratulates the victims and invites them to accept their limited-time prize — by sending some personal information to claim it.
Unfortunately, the prize is really for the attackers: sensitive personal information that can be resold on the dark web or used to gain access to personal accounts.
Why are social engineering attacks online so dangerous?
Social engineering attacks can be very dangerous for both individuals and companies, because in both cases, large amounts of money can be taken from the victim.
In 2019, Toyota Boshoku Corporation, an auto parts supplier for Toyota, lost $37 million dollars in a social engineering attack. The attackers targeted employees in the finance department by posing as higher-level employees. The hackers sent emails from fake — but convincing — corporate email accounts, requesting an account change. This successfully fooled the accountants into transferring large sums of money into accounts controlled by the conniving hackers.
For most people, losing any amount of money can be a huge setback. But having your personal information compromised can be even more dangerous. If an attacker gains your login credentials, social security number, or bank details, they may keep it for their own use or they may sell it on the dark web — where it can be bought and exploited by others, leading to identity theft or additional damage in the future.
Spotting a social engineering attack
To spot an attempted online social engineering attack, it’s helpful to know the different techniques attackers use to influence their victims.
People react to authority and are more likely to obey when requests come from a respected source. This is why cybercrimes often impersonate well-known companies or government agencies like the Internal Revenue Service (IRS) in the US. Always look carefully at emails that claim to be from government or other authoritative sources. Although the IRS knows your personal information, such as your name, address, and social security number, they would never ask you to send it to them in an email.
People react to authority and are more likely to obey when requests come from a respected source.
A more subtle tactic exploits likability. As humans, we’re more likely to trust people we find attractive and pleasant, which can do wonders for peer-to-peer selling. Multi-level marketing companies like Mary Kay and Avon have built entire empires using this tactic. Attackers can impersonate an attractive person on social media and use a compliment as an excuse to make contact. When the victim feels flattered, they’re more receptive to an attacker’s request, which could be for a donation to their “charity” or some other scam.
Knowing the ways we can be influenced makes it easier to recognize social engineering red flags. Requests for certain types of information, like login details, banking information, or your address should also always raise concerns. Put aside emotion and look closely at who is asking for your details — it could save you from being scammed.
Too good to be true
A classic social engineering move is to offer something very tempting that motivates the victim to reveal some information or take some action. This tactic can be used in legitimate ways as well, like when a company offers customers a $10 gift card as a reward for writing a product review.
Attackers take advantage of our familiarity with these legitimate offers and push things further, offering $100 for completing a survey that just so happens to require creating a login. In this example, attackers are hoping that you reuse other login credentials, which they can then use to access your online banking or other valuable accounts.
If you take a moment to think about it, $100 for answering a survey seems like an offer too good to be true. Of course, after you finish the survey, the $100 will prove to be merely a ruse, and you’ll have shared login information with a shady source. Always take time to research tempting offers before taking action. And remember that when something seems too good to be true… it often is.
The most common types of social engineering attacks online
Creative scammers have come up with many types of social engineering attacks, using different techniques and entry points to gain access to their targeted information. Unfortunately, these scamming techniques are all too common. But learning about the variety of social engineering tactics out there will help you recognize an attempt, should you come across one yourself.
 Spam emails
Spam emails
You might think of spam simply as a tab in your email inbox, but not all spam emails are successfully filtered out of sight. Well-crafted spam emails can slip past email server screenings and into your inbox, where they can appear like a credible message.
Social engineering emails usually try to entice you into clicking links to fake websites, downloading malicious attachments, or responding with the sort of sensitive information they sender is looking for. Reading up on email security can help prepare you to spot the difference between sneaky spam mail and trusted sources.
 Baiting
Baiting
Just as we bait mouse traps with cheese, an attacker using baiting social engineering leaves something enticing in view of their target. Sometimes it’s a physical item, like a USB flash drive left in a public place labeled “confidential” in order to spark someone’s curiosity. Once the flash drive is inserted into the victim’s computer and opened, malware infiltrates and infects the host device as well as any connected servers.
Baiting can also take place online, with something like a movie download used as bait. Once the file is downloaded and opened, the hidden malware gains access to the computer.
 Phishing
Phishing
Probably the most common type of social engineering, phishing happens when an attacker impersonates a legitimate company or organization and targets a victim over email, chat, or online ads. The email or message usually directs the victim to a fake landing page, complete with correct company graphics. The page asks for login verification or requests a password change due to suspicious activity.
If the victim complies, the attacker gains access to this login data and can use it to try to log into other websites as well, depending on how often the victim uses different passwords for different sites.
Catfishing is another common social engineering strategy in the phishing category. Catfishing involves impersonating a desirable person on a dating site or social media platform and then wooing potential victims.
Strong emotions are part of any romance, and these emotions can cloud intuition and obscure warning signs. Once the victim is on the hook, the catfisher will figure out a scenario to exploit them for money.
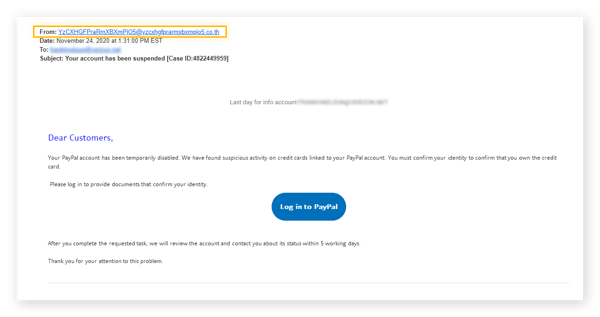
What does a phishing email look like? In the image below you can see an email from an attacker pretending to be from PayPal. The email claims that there has been suspicious activity on a PayPal account and that the account has been suspended until the user logs in and submits documents to confirm their identity — using fear and urgency to motivate action.
 A phishing email mimics a brand’s style but clearly comes from a fake email address.
A phishing email mimics a brand’s style but clearly comes from a fake email address.
But if you look closely at the sender’s email address, you’ll see a long string of numbers and letters, and the domain is certainly not PayPal. The email is also addressed “Dear Customers,” which is oddly general given the private nature of the email.
The login button in this email will not redirect to PayPal, but to a fake landing page where the attackers can collect login information. And, if they’re lucky enough, they can capture official documents such as ID cards or passports to confirm the user’s identity.
Spear phishing
Social engineering phishing scams are often sent to hundreds of potential victims, hoping that someone will click the link. But sometimes the attacker does background research on their potential victims, narrowing it down to a more specific group of people or even one person.
This type of focused, or narrow, attack is known as spear phishing, and it’s significantly more effective than you might expect. 50% of people targeted open spear phishing emails, compared to an open rate of only 3% for regular phishing messages.
Take Amazon founder Jeff Bezos. He’s one of the biggest fish in the sea, and so far removed from everyday problems you might think he could never be phished. But in 2018, Bezos was targeted by the Saudi Crown Prince Mohamed bin Salman.
The two met in person, built a connection, and exchanged phone numbers. The Crown Prince then sent a video file over WhatsApp, which after being downloaded, started transmitting large amounts of Bezo’s data without authorization. Bezos may be the leader of a massive tech company, but he’s still human and so susceptible to manipulation and social engineering.
 Pretexting
Pretexting
Pretexting social engineering attacks involve inventing a scenario, or pretext, to target the victim. The attacker usually impersonates someone authoritative who can request information. An effective pretexting attack requires background research and preparation on the attacker’s end. They need to be able to accurately answer the victim’s questions and appear legitimate.
A common example of pretexting is when an attacker impersonates someone from a company’s IT department. The attacker reaches out to an employee within the company, identifies themselves, and requests remote access to their computer or their login credentials to update a piece of software.
Depending on whom they’ve targeted, the attacker could then have access to all of the company’s financial records or employee data. They can hold this information hostage using ransomware, or use it to carry out the next step in a scheme.
In 2017, Classic Ether Wallet, designed to store the cryptocurrency Classical Ethereum, was the victim of a social engineering attack. A hacker impersonated the owner of Classic Ether Wallet and gained access to the domain as well as private keys that allowed him to transfer money out of victims’ accounts and into his own server.
 Vishing
Vishing
Vishing is the same concept as phishing, but conducted over the phone — that is, voice phishing. In a vishing attack, the phone number used will often be blocked or disguised as coming from a help desk or support center. Sometimes voice-changing technology is used to try to imitate a specific person.
A vishing attack usually seeks to manipulate victims into revealing their login information or gain access to the victim’s computer. Attackers often pose as someone from customer service or tech support, calling to install an update or fix a bug that requires the victim to grant access or reset their login credentials.
In 2019, a popular vishing scam occurred in which attackers disguise their caller IDs to appear to be calling from Apple. The call was automated and warned the victim about a security breach at Apple, instructing them to call a different number before performing any actions on their phone.
When victims called the number provided, they received an automated welcome message mimicking the Apple customer support center, complete with an estimated wait time. Once victims actually reached a person, the attackers attempted to obtain their Apple ID login credentials.
These attacks took advantage of people’s widespread use of Apple products, Apple’s brand authority, and the fear and urgency of a security breach — knowing that people would respond and take action. Apple has since warned their customers that they never make unsolicited calls, and that they should never answer calls that appear to come from them.
 Quid pro quo
Quid pro quo
Quid pro quo means trading something for something else. Attackers are happy to offer you something in a quid pro quo social engineering attack, and in return they hope to get your login credentials or access to your computer.
Help is commonly offered in quid pro quo attacks, be it technical assistance, access to a special document, or solving a problem you didn’t even know you had.
After the second Boeing 737 Max airplane crash in 2019, hackers capitalized on people’s high emotions and fear by sending out emails from accounts posing as ISGEC, an engineering company. The hackers claimed to have accessed a leaked document on the dark web that listed the crashes before they happened, along with future crashes that had yet to take place.
The hackers urged people to open the document and — for the sake of their families and loved ones — check to see that no one they knew planned to take any of the listed flights. Of course, the list wasn’t real, and downloading the file infected the victim’s computer with malware that allowed the hackers to access data they wanted.
Famous social engineering attacks
Social engineering attacks don’t happen only to average, unsuspecting people. They happen to big tech companies and famous people, too. Unfortunately, when they happen to large companies, it’s often customer data that’s at risk.
Barbara Corcoran, a successful investor and Shark Tank judge, lost $380,000 in a 2020 social engineering attack. Using pretexting, the scammer impersonated Baraba’s personal assistant by using an email address that swapped just one letter. The attacker emailed Corcoran’s bookkeeper, requesting the renewal of a payment related to a real estate investment. The scam was discovered when the bookkeeper sent a follow-up email and CC’d the actual personal assistant on the message.
We’re all humans with emotions that can be stirred and agitated, and we all react to beauty and authority and can be tempted by urgency and reward.
In 2013, Target was the victim of a massive social engineering attack, with the hackers gaining access to the payment information of 40 million people. The attackers wormed their way in through a phishing email to a refrigerator company that Target was partnering with. The attackers then installed malware on the refrigerator company’s computers and waited for someone to enter their login credentials and gain access to Target’s servers.
From there, the hackers were able to navigate Target’s internal systems and find vulnerabilities to copy people’s payment data and dump it onto their own external server.
In 2015, Ubiquiti Networks, a Wi-Fi component manufacturer in San Jose, lost $39 million dollars when a hacker impersonated an employee and targeted the finance department. Posing as a vendor, the attacker managed to convince a subsidiary of Ubiquiti’s finance department to change payment details, funneling the money into the hacker’s account.
Although Ubiquiti initially lost over $47 million dollars, they were able to recover $8 million — small consolation amid a devastating loss.
Who's most at risk of falling victim to social engineering?
In reality, everyone is vulnerable to social engineering attacks. We’re all humans with emotions that can be stirred and agitated, and we all react to beauty and authority and can be tempted by urgency and reward.
We shouldn’t think of these qualities as weaknesses — after all, we developed them for evolutionary reasons. Instead, we should learn how others can manipulate them and train ourselves to spot the warning signs. The elderly are often targeted for social engineering attacks, because they’re not always familiar with modern technology and are less likely to notice something suspicious.
Tips to avoid becoming a victim of social engineering
Just like you can practice good habits to prevent pickpocketing (keep that zipper zipped!), you can learn useful tips and practices for social engineering prevention.
But if you think you may have been a victim of social engineering or are looking to add an extra layer of protection, AVG BreachGuard can help. BreachGuard will notify you the moment any of your personal information leaks online, and it will monitor around the clock for future incidents — like your own personal internet watchdog.
Report and delete suspicious emails
Found someone phishing in your inbox? Don’t just mark the suspicious email as spam. Depending on the content of the email, you should take action by reporting the internet scam. A good follow up action is to read up on how to report cybercrime so that you’re prepared for the future.
In the US, the Federal Trade Commission (FTC) recommends that you report phishing emails by sending them to the Anti-Phishing Working Group at reportphishing@apwg.org. If you’re in the UK, you can forward them to the Suspicious Email Reporting Service at report@phishing.gov.uk.
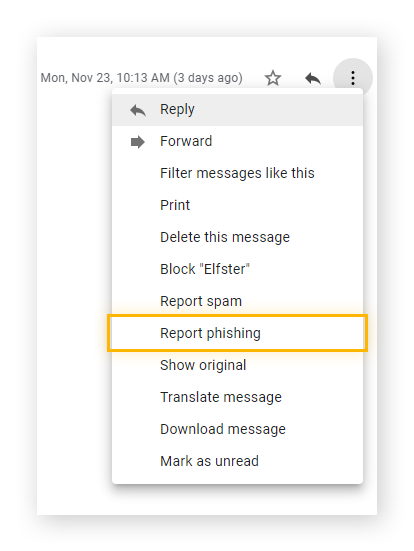
If you use Gmail, there’s a built-in way to report phishing. Go to the top right corner of the email and click on the three vertical dots next to “reply.” Then select “Report phishing” from the drop-down menu. You can also take preventive security steps by learning how to stop spam email from even reaching your inbox.
Research sources and websites
If you receive an email with a surprisingly dramatic message (claiming, say, that your social security number has been compromised), remember to check the source of the email before panicking. Scammers often use email addresses that look totally bogus, like a jumble of letters and numbers, hoping you’ll be too distracted by the message to notice. Also, remember that urgency and fear are manipulation tactics.
More sophisticated scammers use email addresses that are almost perfect, like the social engineering scam mentioned above with Barbara Corcoran. In these cases, you’ll need to look closely and check for any typos in an otherwise legitimate looking email address.
If the social engineering attack tries to lead you to a specific website, always check to see if the site is safe before clicking the link or typing in the address. A quick web search of the URL can unveil reports of scams related to the web address. You should also be wary of sites that are missing the “s” in HTTPS (at the beginning of the web address) — the “s” stands for “secure.”
Install a trusted antivirus
Antivirus software has evolved alongside cybercrime, and it’s one of the best tools to have in your toolkit while using the internet. AVG offers free antivirus software that detects and blocks viruses, ransomware, and other malware. It can even catch malicious downloads and infected email attachments before they make it to your computer — especially useful if you’ve fallen into a social engineering baiting trap while trying to download a movie.
Adding AVG AntiVirus FREE to your cybersecurity toolkit costs you nothing and adds a whole new layer of protection between you and the viruses and scams lurking around the internet.
Use a private Wi-Fi connection or a VPN where possible
Even though logging into free airport Wi-Fi and replying to work emails seems like a better idea than terrible pizza at the food court, remember that the Wi-Fi network won’t be a private connection.
Many other people will be sharing the same network as you, and that makes your personal (or work) information vulnerable to attacks. While accessing sensitive information, especially private details like your online banking credentials, be sure to always use a private connection.
Another great tool to use is a VPN (virtual private network). A VPN, like AVG Secure VPN, encrypts your connection to the internet so you can use public Wi-Fi safely. It also disguises your IP address so that your online activity can’t be linked to your real identity and location. Installing a VPN gives you an extra layer of protection against malicious intent both at home and out in public.
Implement multi-factor authentication
Using two-factor authentication can keep you out of the low-hanging-fruit group of internet users that hackers love to target. Two-factor authentication requires you to verify your identity in two separate places, such as on your computer and your phone, or even with a physical security key.
It’s unlikely that a hacker can access your computer and your phone at the same time, so multi-factor authentication is a great roadblock to prevent someone from gaining access to your accounts. Seeing an authentication request on your phone when you haven’t tried to log in on your computer is also a clear red flag that something suspicious is happening.
Always use strong passwords
If you fall into a social engineering trap and the attacker gains access to your login information, you don’t want them to be able to use it to access your other password-protected accounts. That means that you shouldn’t use the same passwords across different accounts, and you should always create strong passwords.
If the compromised password happens to be for your email account and was “sparkleKitten456,” and the password you use for online banking is “123kittenSparkle,” it’s likely that the hacker will be able to figure out your other password and access your banking information as well. Being lazy with password creation is like taping your door shut instead of locking it — not very effective in the event of an attack.
If you’re not ready to memorize a dozen different complex passwords, try a password manager.
Use an antivirus in the fight against social engineering
It may seem like the internet is crawling with malicious people trying to manipulate your emotions long enough to steal your data. But preventive measures go a long way in the battle against social engineering threats. Reading up on existing social engineering techniques makes it much easier to spot them in action and makes you much less likely to take the bait.
Besides education, one of the best preventive steps you can take against social engineering is using strong antivirus software. AVG AntiVirus FREE scans your computer and network, detecting and thwarting any viruses, spyware, ransomware, or other malware that a hacker may be trying to sneak in.
AVG AntiVirus FREE also blocks unsafe email attachments, links, and downloads, so that you won’t even be able to click on them by mistake. We’re all human, trying to navigate the internet with whatever biases we may have — so it’s nice to have an extra layer of security in the event we do fall victim.

 A phishing email mimics a brand’s style but clearly comes from a fake email address.
A phishing email mimics a brand’s style but clearly comes from a fake email address.





