What is ransomware?
Ransomware is malicious software that encrypts files on your computer or locks your device and demands a ransom in exchange for decryption. Ransomware attacks target individuals, businesses, and government agencies, and can result in the loss of sensitive data or critical information. Ransomware spreads through phishing attacks, infected websites, or other methods of hacking.
Ransomware hackers often demand the ransom in Bitcoin or other cryptocurrency, and there’s no guarantee that paying up will get your files decrypted.
So, is ransomware a virus? No, it’s a different type of malicious software. Viruses infect your files or software and self-replicate. Ransomware scrambles your files to make them inaccessible and unusable, then demands you pay up. Ransomware and viruses can both be removed with strong antivirus software, but if your files have already been encrypted, it’s unlikely you’ll get them back.
How does ransomware work?
Ransomware works by preventing you from accessing your data. After gaining access to your computer, it silently encrypts your files, and then demands a ransom payment in exchange for returning access to the encrypted data. At this point, it’s usually too late to recover your files, as they’re already encrypted.
How a ransomware attack happens
Ransomware attacks happen like this: First, malware infiltrates your computer through malicious attachments or links in phishing emails, infected websites, fake ads, browser hijackers, drive-by-downloads, or by exploiting a security vulnerability. Then, once embedded in your system, the ransomware begins encrypting your data. Finally, it reveals its presence with a ransom demand.
After infecting your PC, some ransomware strains can spread to your contacts, then their contacts, and so on, infecting everyone along the way.
Here’s how ransomware attacks happen:
Step 1: Device infection
Ransomware spreads quickly and hits hard. Here are a few ways ransomware can infect your device:
-
Social engineering attacks: Social engineering techniques fool people into downloading malware from a fake attachment or link purportedly sent by a reputable company or institution. When you download one of these malicious files and open it, you’ll be infected with ransomware.
-
Malvertising: Malicious advertising injects ransomware, spyware, and viruses into ads and advertising networks. Hackers will even buy ad space on popular, legitimate websites (including social media networks or YouTube) to spread ransomware.
-
Exploit kits: Cybercriminals can package prewritten code into a ready-to-use hacking tool. These kits are designed to exploit vulnerabilities and security holes caused by outdated software.
-
Drive-by downloads: Some malicious websites don’t even require a click — they silently download malware in the background while you’re browsing an innocent-looking website.
For example, you may receive a ransomware-infected email that looks real. It’ll ask you to download an invoice or other important document, like a PDF or Excel file.
However, once you click it, it acts like a .exe file — these files are reserved for executing software installations, so they have permission to make changes to your computer. Avoid running them if you aren’t sure of the source. Sophisticated hackers can make a file look like a PDF, even if it’s really an executable.
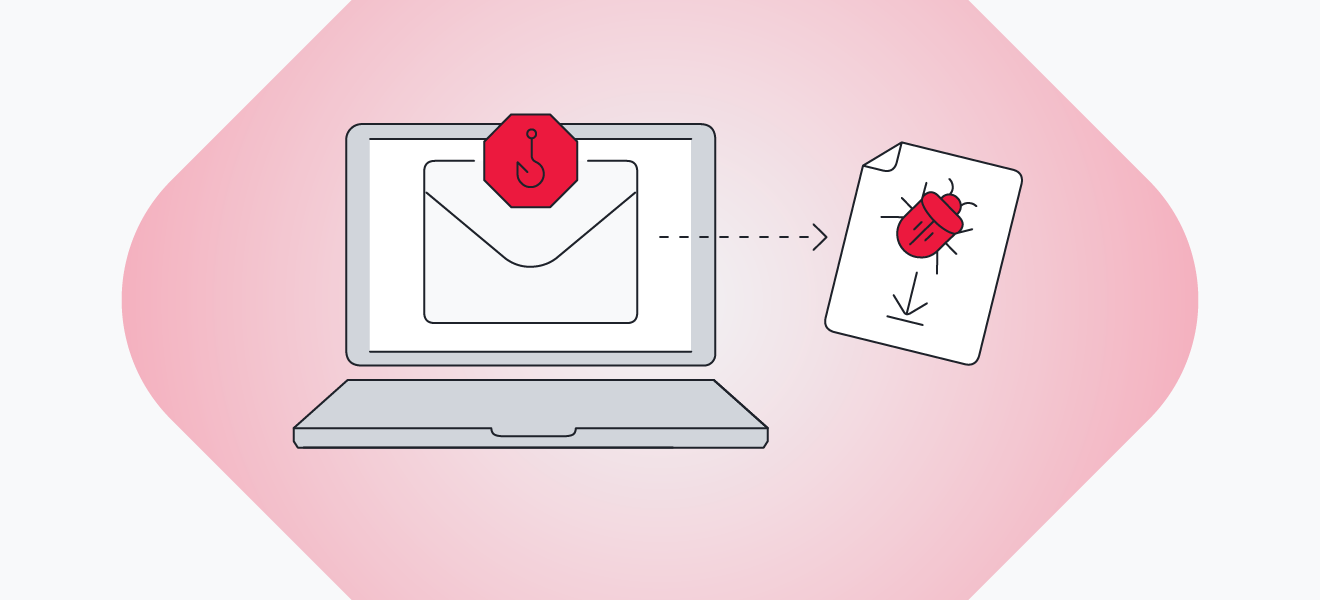 Ransomware can infect your device through phishing emails or malicious attachments.
Ransomware can infect your device through phishing emails or malicious attachments.
Step 2: Data encryption
After your computer is infected, your data will be encrypted so you can’t access it anymore. The malware contacts the hacker’s server, generating a pair of keys — a public one to encrypt your files, and a private one stored on the hacker’s server for decrypting them. This is also known as asymmetric encryption.
Once the ransomware hits your hard drive, it’s too late to save your data. The ransomware starts running and encrypting your files, and only reveals itself once the damage is done.
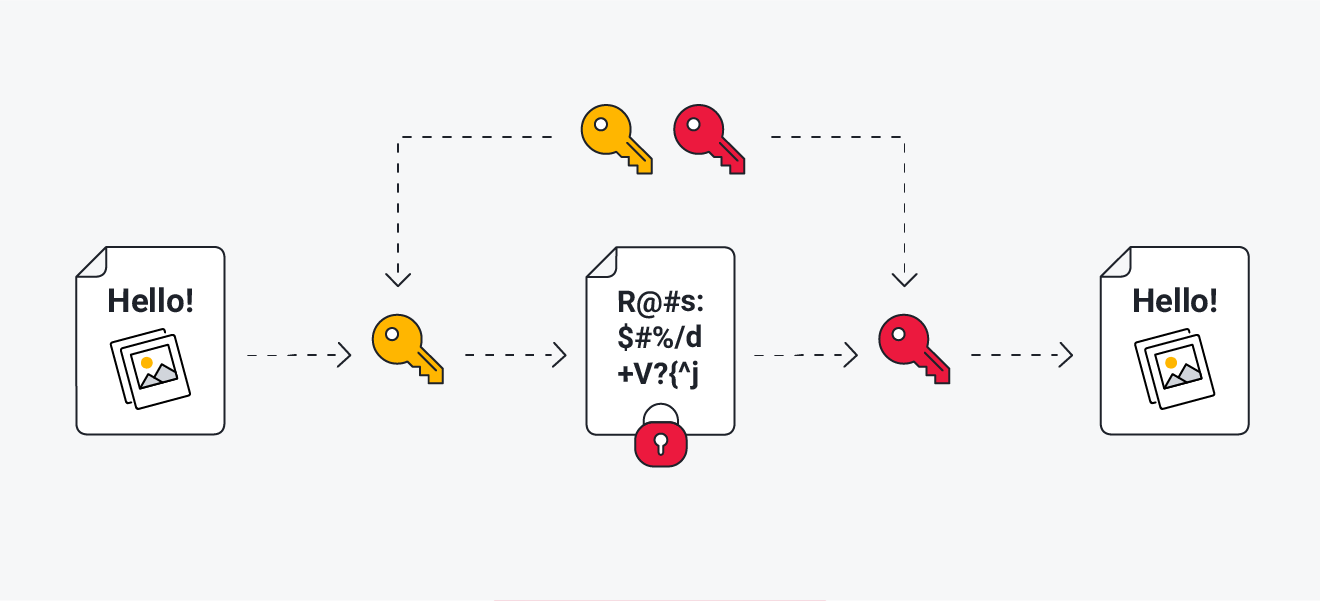 Ransomware typically uses asymmetric encryption on your files.
Ransomware typically uses asymmetric encryption on your files.
Step 3: The ransom note
After your files are encrypted, a ransom note pops up on your screen, telling you how much you’re expected to pay and how to transfer the money. Then, the clock starts ticking — you’ll typically have a few days to pay the ransom, and the price goes up if you don’t make the deadline.
But, there’s no guarantee that you’ll get the files back if you pay the ransom, nor is it certain that the hackers will delete the data. For these reasons, you shouldn’t pay the ransom.
 Don’t pay the ransom after a ransomware infection, as payment doesn’t guarantee your files will be decrypted.
Don’t pay the ransom after a ransomware infection, as payment doesn’t guarantee your files will be decrypted.
You won’t be able to open your encrypted files, and if you try to do so, you’ll get an error message saying your file can’t be loaded, or it’s corrupted or invalid. That’s why it’s a good idea to regularly back up all your important files in case you’re ever infected with ransomware.
Types of ransomware
Ransomware comes in all shapes and sizes. Some variants are more harmful than others, but they all have one thing in common: ransomware — by definition — requires a demand of payment.
 Cryptomalware
Cryptomalware
Cryptomalware or encryptors are the most common type of ransomware. It’s called crypto-ransomware or cryptomalware, not because cryptocurrency is involved, but because files become encrypted and impossible to open. This type of malware can do a lot of damage, both financial and otherwise, by using super-strong data encryption methods.
The total amount of money extorted in the first half of 2023 alone was around $450 million — almost twice as much as the first half of 2022. Targets of cryptomalware are usually larger companies or institutions, with average ransom payments topping $1 million for some strains, such as Cl0p and BlackCat ransomware. Users are often directed to a payment portal in a Tor browser, like with SamSam ransomware.
But the damage is more than just monetary. In late 2020, Ryuk crypto ransomware put thousands of lives at risk when it hit hospitals and blocked medical staff from accessing patient files.
 Lockers
Lockers
Lockers infect your operating system to completely lock you out of your computer and make it impossible to access any apps or files. And the sophistication of the protocols used to encrypt the system means it’s practically impossible to recover without the right decryption key. Many victims of locker malware will seriously consider paying the ransom, but it’s not likely they’ll get their files back if they do.
 Scareware
Scareware
Scareware is fake software (like a fake antivirus or cleaning tool) that claims to have found issues on your PC and demands money to fix them. Some scareware variants lock your computer, while others flood your screen with annoying alerts and notifications. Other times, it slows down your computer and sucks up its resources.
Even if money is involved, that scareware demanding payment might not be ransomware. It might just be tricking you into making a payment without actually doing any damage to your computer. But that doesn’t mean you should take it any less seriously — malware rarely tells you how much damage it’s doing to your computer behind the scenes.
 Doxware
Doxware
Doxware (or leakware) threatens to publish (or dox) your stolen information online if you don’t pay up. We all store sensitive files on our PCs — from contracts and personal documents to embarrassing photos — so it’s easy to see why that might cause panic.
 Ransomware as a Service
Ransomware as a Service
RaaS (Ransomware as a Service), like MedusaLocker, is malware hosted anonymously by a hacker who handles everything — distributing the ransomware, collecting payments, managing decryptors — in exchange for a cut of the ransom. Working as a RaaS, LockBit was the most active ransomware group in 2022.
 Android ransomware
Android ransomware
Your Android mobile devices aren’t immune to ransomware either. Android ransomware is most likely to be a locker, which prevents you from accessing your device via the UI or a pop-up that won’t go away.
There’s even a WannaCry copycat — WannaLocker — which spreads on gaming forums and targets Android devices in China. Since data can easily be restored by syncing devices, cybercriminals often prefer blocking your smartphone instead of just encrypting files.
As ransomware has grown, it has increasingly targeted Windows, making Android ransomware comparatively rare. But be sure to watch out for suspicious Android apps anyway.
 Mac ransomware
Mac ransomware
Even though Apple devices are more resistant to malware than Windows PCs, Mac ransomware may also be on the rise. The LockBit ransomware group is actively working to break Mac’s security defenses, which are still holding strong, thankfully. But in cybersecurity, it’s easier to break a system than defend it. So, it’s only a matter of time.
Examples of ransomware attacks
The first recorded ransomware attack occurred in 1989, when evolutionary biologist Joseph Popp infected floppy disks with the AIDS Trojan and distributed them to fellow researchers. The malware waited until victims booted their PCs 90 times before encrypting all system files and asking users to pay $189 to undo the damage. Luckily, experts came up with tools to remove the malware and decrypt the impacted files.
In recent years, a range of organizations like hospitals, governments, and large corporations have been hit with large-scale ransomware attacks that have forced them to choose between paying thousands of dollars in ransom to cybercriminals or absorbing millions in recovery costs.
Rhysida
Rhysida emerged in 2023 and has already successfully targeted 50 organizations. Rhysida works fast by efficiently leveraging the victim’s CPU and only encrypting significant portions of targeted data, rather than all of it. Rhysida’s ransom note positions themselves as the “cybersecurity team” that will help recover the data and keep it from leaking.
Rhysida has attacked institutions like the British Library via phishing techniques that let the attackers gain remote access to employee information.
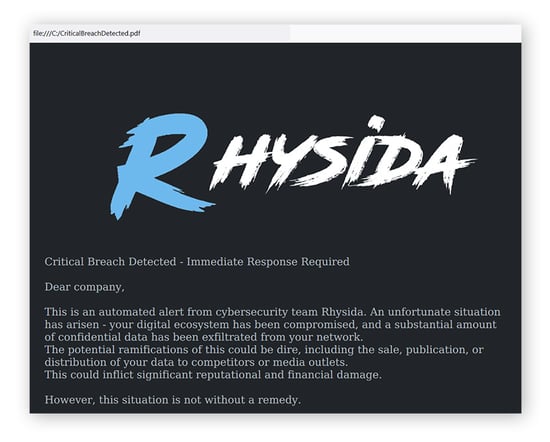 An example of the ransom note from a recent version of Rhysida ransomware. (source: decoded.avast.com)
An example of the ransom note from a recent version of Rhysida ransomware. (source: decoded.avast.com)
Clop
Clop (sometimes stylized “CL0P”) is a ransomware group that took advantage of a zero-day vulnerability in MOVEit file transfer software in May 2023.
Clop spreads via remote access trojans (RATs), collecting system information and gaining access to the targeted network, which ultimately allows for covert data theft. Clop has also spread by — you guessed it — phishing. All it took was one click, and as much as $20 million was lost. It’s reportedly managed to extort payouts of up to $500 million.
BlackCat
BlackCat ransomware leverages advanced encryption techniques that operate differently based on the file extension and use patterns of encryption to make files unusable or inaccessible with the least amount of effort. Activity peaked in 2022, but it’s still a threat today — avoid BlackCat by looking out for phishing emails and texts, improving the strength of your passwords, and disabling macros in Microsoft Office.
Ryuk
Ryuk resembles the activities of older ransomware attacks like WannaCry, with the particularly nefarious characteristic of gaining as much access as possible before it encrypts anything. It’ll even detect backups of files and specifically prioritize encrypting them. Also mainly spread via phishing, Ryuk ransomware has been used to target hospitals and compromise access to patient records. Attacks of this sort happened during the coronavirus pandemic and even disrupted chemotherapy regimens for cancer patients.
CryptoLocker
CryptoLocker was a ransomware attack in which multiple victims reported paying the ransom and not getting their data back. This ransomware also raised the ransom after a certain deadline, increasing the incentive to pay sooner. Dutch cybersecurity firm Fox-IT managed to extract the keys and make decryption possible, but several CryptoLocker clones have popped up since.
Hive
The saga of Hive ransomware is thankfully winding down, with the group shut down and cyberattacks halted in early 2023. The end of their operations came when a vulnerability was found in their encryption tool. But not before they’d crippled victims and institutions around the world and amassed over $120 million in ransom payments.
WannaCry
After infecting more than 10,000 organizations and 200,000 individuals in over 150 countries, the WannaCry strain earned its reputation as the most widespread ransomware attack of its time. It used an exploit known as EternalBlue, which takes advantage of a Windows SMB (Server Message Block, a network file-sharing protocol) vulnerability labeled as MS17-010. By the time it was shut down, WannaCry had attacked over 100 million Windows users.
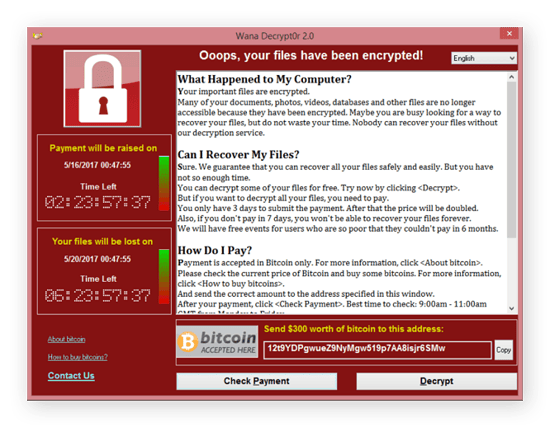 The WannaCry ransomware note. (source: Wikimedia Commons)
The WannaCry ransomware note. (source: Wikimedia Commons)
Petya
The Petya ransomware attack (and similar strains dubbed Petna, NotPetya, EternalPetya, or Nyetya) gave everyone a big scare, but it was far less damaging than WannaCry. Petna affected victims mainly in Ukraine (more than 90% of attacks), but there have been attacks in the US, Russia, Lithuania, Belarus, Belgium, and Brazil as well.
Other well-known strains of ransomware include Bad Rabbit, Cryptolocker clones, GoldenEye, Jigsaw, and Maze. Some, like REvil ransomware, have been stopped, but more are popping up all the time.
Who does ransomware target?
Ransomware tends to target organizations and institutions, because a sizable ransom can be demanded from these victims — often millions or tens of millions of dollars. But ransomware can impact anyone, from institutions (both private and public) to individuals (both high- and low-profile), including:
-
Healthcare institutions, hospitals, and pharmacies
-
Universities, colleges, and other educational systems
-
Construction companies
-
Government institutions, both federal and local
-
Media companies
-
Small and medium-sized companies
-
Utility infrastructure
-
Legal services
-
Financial services
-
Manufacturing companies
-
Individuals
If you aren’t protecting yourself against ransomware with updated software and a reliable anti-ransomware tool, you can be targeted by ransomware. Ransomware is often designed to take advantage of security holes in older software and unsecured devices. When support for Windows 10 officially ends in 2025, we strongly recommend that you update your operating system. If you don’t, it could put you at increased risk of ransomware infections.
While installing security updates is generally quick and easy for regular users, larger organizations may be more vulnerable. They often run sensitive, custom software and need to deploy the fixes on a massive number of devices, making the update process more difficult and time-consuming.
Some organizations also lack the funds to afford new software. Hospital budgets are expected to save lives, not computers — but those can be one and the same when their systems get taken over and hospital staff are locked out of patient records.
Cybercrime is the top concern for organizations working with sensitive data, but that doesn’t mean regular users are safe. Your family photos and personal files are also valuable to hackers, and they can be used against you.
How to prevent ransomware
The best way to avoid ransomware and other malware is to practice smart digital habits. That means avoiding suspicious websites, links, attachments, and spam, as well as practicing good email security. Here are some additional tips to help you learn how to protect against ransomware:
Back up your important files
Back up important files or clone your entire hard drive to save everything. You can use an external drive, a cloud service, or both. Choose from Dropbox, Google Drive, Mega, or another free cloud service to securely store your important documents and photos. Find a service that lets you roll your data back to a previous version in case something happens to your account.
If cybercriminals lock up your important files, but you have a backup stored safely, then they have no leverage. You can simply remove the ransomware, restore your files, and ignore any ransom demands.
 Backing up your files takes the sting out of ransomware attacks.
Backing up your files takes the sting out of ransomware attacks.
Use an updated antivirus
Antivirus software offers essential protection against anything trying to mess with your computer. Try AVG AntiVirus FREE for 24/7 protection against ransomware and other types of malware. And AVG Internet Security offers even greater defense against ransomware with its powerful Enhanced Ransomware Protection feature.
Update your operating system
Security updates are a vital component in your computer’s defense against online threats. Outdated software makes you more vulnerable to all kinds of malware, including ransomware. Always keep your operating system and apps updated — use auto-update wherever possible and install updates as soon as they’re available.
How to get rid of ransomware
Unless you’re locked out of your PC, deleting ransomware is pretty easy. In fact, it’s the same as removing a virus or any other common type of malware. But removing the ransomware will not decrypt your files. Beware that some of the methods below can help you recover your device, but will permanently erase all data stored on it — encrypted or not.
Here’s how to get rid of ransomware on different platforms:
On Windows
To get rid of ransomware on Windows, the first thing you should do is disconnect from the internet and run anti-ransomware software. If you manage to quarantine and delete the software, you can be extra safe by using System Restore. Windows creates restore points periodically, giving you options to go back to a point before the malware hit.
Things are a bit more complicated if your PC is infected with a locker, which prevents you from entering Windows or running any programs.
There are three ways to fix a locker infection on a Windows PC:
-
Do a System Restore to restore Windows to a point in time where your PC was safe: Turn your PC on and hold the Shift key to enter the recovery screens. Select Troubleshoot > Advanced Options > System Restore.
-
Run your antivirus program from a bootable disk or an external drive.
-
Reinstall your operating system.
On Mac
Getting rid of ransomware on Mac involves isolating the device by starting up your Mac in safe mode and running antivirus software. If this doesn’t get rid of the ransomware, your best option is to wipe the hard drive and restore from a backup made before you got infected. The amount of data you’ll lose will depend on how long ago your last usable backup was made.
On Android
To remove ransomware from an Android device, first quarantine it by turning on flight mode. Then, uninstall any apps you don’t recognize by opening device Settings and opening your Apps list. After you remove any unknown or suspicious apps, run an anti-malware tool to ensure the infection is removed completely. Then, you can begin the process of recovering as much data as you can salvage.
On iPhone
The first step when removing ransomware from an iPhone is to cut it off from all other devices; unplug it and go into airplane mode. Remove temporary browsing files and run antivirus software. Consider resetting the phone and restoring from a backup to ensure the ransomware has been completely purged.
Removing ransomware from any device is similar to removing other malicious software — download trusted antivirus software, run a scan to identify the ransomware, then quarantine or delete the malware. Though it’s trickier, you can also remove malware manually.
A reliable antivirus tool like AVG AntiVirus FREE will not only remove ransomware and other malware as soon as it’s detected on your system, but it’ll help prevent these infections from happening in the first place.
How to recover encrypted files
Some free ransomware decryption tools can help you recover files infected with the ransomware strains Babuk, Fonix, HermeticRansom, TargetCompany, and others. But if you regularly back up your data, you shouldn’t need to worry much about ransomware recovery. Simply delete the ransomware then restore your files from the backup.
If you don’t have anything backed up, you might be out of luck. It’s sometimes possible to crack 32-bit and 64-bit encryption, so you might get lucky if that’s what the cybercriminals used. Additionally, cybersecurity researchers have been able to crack some ransomware strains and replicate their decryption keys.
Prevention — using an antivirus and regularly backing up your data — is the best way to protect yourself from ransomware attacks.
But these days most types of ransomware use 128-bit or 256-bit encryption (and sometimes a combination of both). This complex level of encryption is also used by servers, browsers, and VPNs to protect your data, because it’s highly secure.
If your files are infected with a ransomware variant using one of these highly secure encryption methods, recovery is nearly impossible. That’s why prevention — using an antivirus and regularly backing up your data — is the best way to protect yourself from ransomware attacks.
Those who have already fallen victim to ransomware should find out which strain of ransomware they’ve been hit with and seek help from the authorities. Do not pay the ransom as there is no guarantee you’ll get your data back, and the monetary value of the ransom is probably far greater than that of the data you’ve lost.
Should you pay ransomware?
No. We advise that you don’t pay the ransom. Remember, these are cybercriminals you’re dealing with, and there’s no guarantee they’ll keep their promise. Paying ransom demands tells hackers that ransomware is a profitable business, encourages them to keep using ransomware, and funds other cybercrime.
In some instances, the files held hostage by ransomware can’t actually be decrypted. That was the case with Petya — the ransomware’s encryption algorithm was irreversible. While cybersecurity professionals usually recommend not paying the ransom, not everyone listens. And when businesses face even steeper recovery costs if they don’t pay, they sometimes give in.
Prevent ransomware with cybersecurity software
Rather than worrying about what to do when ransomware strikes, get a good antivirus with built-in ransomware protection so you never have to worry about paying a ransom in the first place. AVG AntiVirus FREE helps protect against ransomware, viruses, phishing, and all kinds of other malicious threats. Start your ransomware protection today with AVG AntiVirus FREE.

 Ransomware can infect your device through phishing emails or malicious attachments.
Ransomware can infect your device through phishing emails or malicious attachments. Ransomware typically uses asymmetric encryption on your files.
Ransomware typically uses asymmetric encryption on your files. Don’t pay the ransom after a ransomware infection, as payment doesn’t guarantee your files will be decrypted.
Don’t pay the ransom after a ransomware infection, as payment doesn’t guarantee your files will be decrypted. An example of the ransom note from a recent version of Rhysida ransomware. (source: decoded.avast.com)
An example of the ransom note from a recent version of Rhysida ransomware. (source: decoded.avast.com) The WannaCry ransomware note. (source: Wikimedia Commons)
The WannaCry ransomware note. (source: Wikimedia Commons) Backing up your files takes the sting out of ransomware attacks.
Backing up your files takes the sting out of ransomware attacks.




