What is spoofing?
Spoofing is a type of cybercrime where an attacker imitates a known contact or organization to secure a victim’s trust. Some spoofing attacks target individuals, while others try to fool entire networks. Spoofing attacks often aim to get access to sensitive personal information or bypass security measures.
Email spoofing attacks happen when hackers forge emails so that they appear to be coming from someone you trust. SMS spoofing and caller ID spoofing attacks disguise themselves behind phone numbers belonging to other people or groups.
Meanwhile, IP spoofing and DNS spoofing attacks manipulate internet traffic. Some attacks, such as DNS hijacking, redirect your traffic to malicious websites. Many hackers use IP spoofing to carry out DDoS attacks. Other attacks aim to intercept, stop, or divert internet traffic so that the hacker can access sensitive data.
How does spoofing work?
Spoofing works by masking the source of a given communication. Emails, phone calls, SMS messages, websites, and even internet traffic itself can all be spoofed so that it appears to be coming from somewhere else.
You may have noticed robocallers masking their caller ID with another number, often one that shares your area code. All types of spoofing rely on the same general principle: disguising the origin of the message or data.
 Spoofing attacks mask the source of communications to gain a victim’s trust.
Spoofing attacks mask the source of communications to gain a victim’s trust.
A successful spoofing attack can lead you to malicious websites, steal your data, or trick you into installing malware. But with the right security software, you can automatically detect and block spoofing attacks before they get a chance to trick you.
AVG AntiVirus FREE warns against malicious emails and websites while detecting and blocking malware in its tracks. No matter the goal of the spoofing attack, you’ll be safe against it with AVG.
Spoofing vs. phishing
The difference between phishing and spoofing is that while spoofing disguises the source or origin of a communication so that it appears to have been sent by someone else, phishing uses social engineering methods to trick people into opening messages or clicking links and thereby disclosing sensitive data.
Spoofing and phishing are often linked because attackers tend to use spoofing methods to make their phishing attacks more believable.
While cybercriminals and sinister hackers often combine spoofing with phishing attacks to steal information, not all spoofing attacks are necessarily examples of phishing. Many IP spoofing attacks are designed to infect entire networks with malware, lay the groundwork for future attacks, or enable DDoS attacks.
While scammers first started spoofing caller IDs, they’ve since expanded to include email spoofing, SMS spoofing, and phishing techniques to gain valuable personal details on a much larger scale.
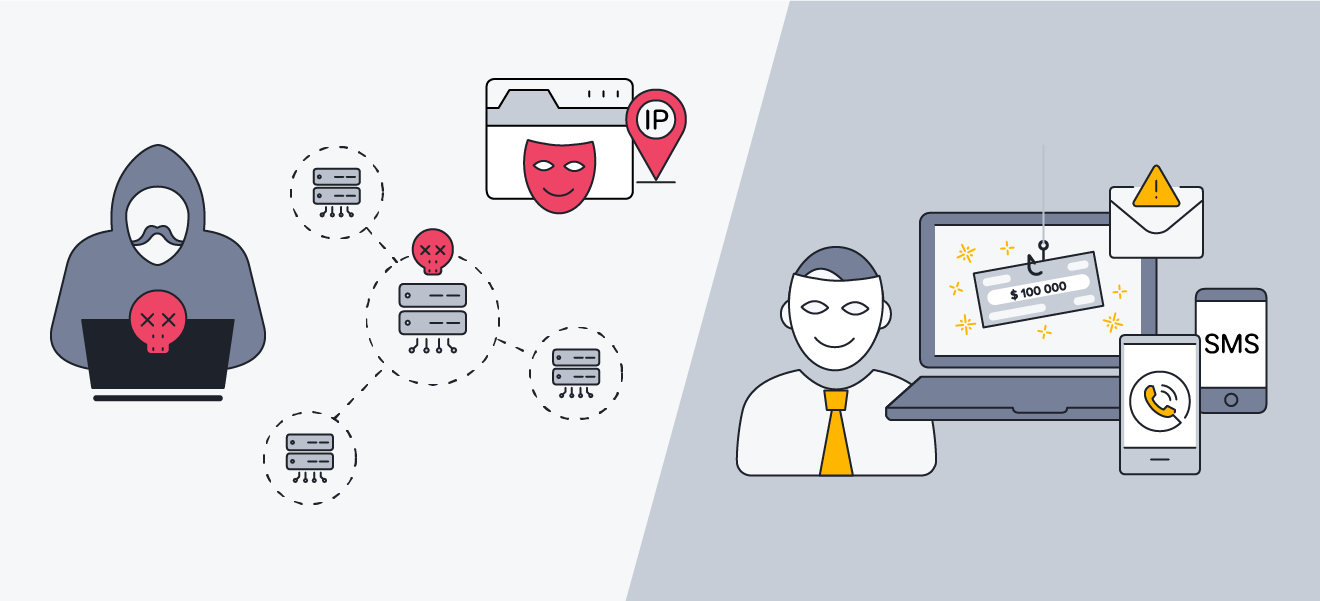 Hackers use spoofing to infiltrate networks and spread malware, while scammers use spoofing to trick victims.
Hackers use spoofing to infiltrate networks and spread malware, while scammers use spoofing to trick victims.
What is email spoofing?
Email spoofing is when attackers make it seem like their emails are coming from another sender — such as a company executive, a well-known bank, or another trusted person or organization.
In email spoofing, hackers alter addresses, signature files, logos or other visual elements of an email to hide its true source or purpose. The most commonly spoofed email properties include:
-
FROM name/address: The sender of the email.
-
REPLY-TO name/address: The email address where a reply will be sent.
-
RETURN-PATH address: A hidden email header that contains instructions for processing bounced emails.
-
SOURCE IP address: The IP address belonging to the email’s sender.
Warning signs of email spoofing
-
Poor spelling and grammar mistakes
Legitimate companies shouldn’t have typos in their emails. If you find typos or awkward phrasing, the email might be spoofed.
-
Misspelled email addresses
To mimic real email addresses, spoofers can swap out certain letters for similar-looking ones, like the numeral 1 for a lowercase L. Look for subtle misspellings — such as “irss[dot]gov” instead of “irs[dot]gov” — or unusual or special characters. Spoofed emails may include Greek letters, for example “bank of amεrica” rather than “bank of america.”
-
Urgency
Email spoofers may try to cause anxiety or panic to push you to make a rash decision. They may threaten you with consequences if you don’t act quickly, like saying your account will be closed or that you’ll face fines if you don’t act now.
-
Generic salutation
Rather than using your real name, the email may address you with “Dear customer” or another generic title. Legitimate emails will often be directly addressed to you.
-
Request for personal information
Legitimate companies don’t need to confirm your username, password, or bank account details via email. The same goes for senior or IT personnel in your company. Spoofing emails will try and trick you into sharing that info with the attacker.
-
Typosquatting
Typosquatting is when hackers register websites addresses using common mistakes people make when typing in URLs to visit legitimate sites. The lookalike site will mimic the real one, but often with the goal of capturing your login credentials or getting you to download malware.
-
Inconsistency
Does the sender’s name match the FROM field or the name in the email signature? Look out for anything that doesn’t match and use this email security checklist.
-
Strange attachments
Many spoofed emails contain attachments that, when opened, will install malware onto your device. Never click or open attachments you aren’t expecting to receive, even if you trust the sender — their email address may be spoofed.
-
No contact info
Legitimate emails will usually include a signature with contact information. Spoofed emails often omit this info.

Telltale signs of a spoofing email: fake FROM email addresses, generic salutations, a sense of urgency, suspicious links, and no contact information in the footer.
What is IP spoofing?
IP spoofing is when an attacker alters the IP address information on a data packet sent through the internet so that the data appears to come from a different IP address. Hackers get the IP address of a legitimate device, then alter the source IP of their traffic to match the legit IP.
Spoofing IP addresses is often used when launching DDoS attacks, so that the actual source IP address is hidden and can’t be traced. IP spoofing generally happens in two ways:
-
Hackers spoof their traffic so it appears to be coming from many IP addresses at once. This prevents server admins from easily tracing the source and blocking the attacks. While IP spoofing can be stopped, it’s much harder to parse out the malicious traffic when it’s coming from thousands of IP addresses at once.
-
Hackers use a botnet to send out thousands of requests, all masked with the victim’s spoofed IP address. Each response to these requests is sent to the victim instead of the botnet device that actually sent it.
Both of these IP spoofing strategies flood the targeted server with traffic, enough to cause shutdowns and other system failures.
Other types of spoofing
-
Website spoofing
Spoofed websites make people believe that they’re interacting with legit sites or trusted companies. At first glance, spoofed sites appear genuine, but scammers cloak URLs and subdomains to give internet users a false sense of security.
-
Caller ID spoofing
Robocallers and other phone scammers spoof their phone numbers so they appear to be coming from a local area code or connected to a trusted organization. When the victim answers these spoofing calls, the spoofer tries to trick them into giving up personal data.
-
SMS spoofing
Spoofers can alter the sender info on an SMS message to make their attacks more believable. Spoofing text messages often contain links that will install malware onto the victim’s device or lead to spoofed websites.
-
GPS spoofing
Fake global positioning signals relay incorrect geolocation coordinates to GPS-enabled devices. People can use GPS spoofing apps for many reasons, like making other GPS-connected apps think they’re in a different place than they actually are.
-
DNS server spoofing
Cyberattackers can manipulate DNS information to divert traffic to different IP addresses, redirecting victims to sites that spread malware, computer worms, and viruses.
-
ARP spoofing
Also known as ARP poison routing, this technique attempts to link a cyberattacker’s MAC address to a legitimate IP address in order to receive data meant for the owner of the real IP address. ARP spoofing is used to steal or modify data and also for man-in-the-middle attacks or HTTP session hijacking.
How to protect yourself against spoofing attacks
-
Stay vigilant
Read emails carefully and be sure you know the sender. Look for fake FROM addresses and Subject lines, spelling errors, or grammar mistakes.
-
Trust your gut
Don’t reply to emails or SMS messages from unknown sources, and think twice before you hand over personal info. Don’t click suspicious links or open strange attachments.
-
Confirm email address and phone numbers
Cross-check email addresses against previously sent emails to see if they’re the same. Always source corporate phone numbers from official websites.
-
Verify links
Hover your cursor over links to check if the URLs lead where you expect them to go.
-
Use strong passwords
Change your passwords regularly. Create long, unique, and strong passwords or passphrases, and then protect them with a secure password manager.
-
Use safe and secure websites
Before entering payment information on a website, make sure the URL has an “s” after the http in the address (https://) and a lock icon to the left of the address field — two important indicators that the website is safe and secure.
-
Update your OS and browser
Use a trusted private browser and always update your operating system to get the latest security patches against known vulnerabilities.
-
Use strong antivirus software
Install the best antivirus software you can find and keep it updated.
Protect against spoofing attacks with a leading antivirus tool
Spoofers use a wide range of tricks to fool you — from malicious email attachments to benign looking but infected websites. AVG AntiVirus FREE keeps you safe against them all. Automatically detect and block attacks and threats like these to keep your data safe and your devices malware-free.

 Spoofing attacks mask the source of communications to gain a victim’s trust.
Spoofing attacks mask the source of communications to gain a victim’s trust. Hackers use spoofing to infiltrate networks and spread malware, while scammers use spoofing to trick victims.
Hackers use spoofing to infiltrate networks and spread malware, while scammers use spoofing to trick victims.





