What is Google dorking?
Google dorking, also called Google hacking, is a search-hacking technique that uses advanced search queries to uncover hidden information in Google. Google dorks, or Google hacks, refer to the specific search commands (including special parameters and search operators) that when entered into the Google search bar reveal hidden parts of websites.
When Google crawls the web to index pages for its search engine, it can see parts of websites that normal internet users can’t. Google dorks and Google hacks uncover some of that hidden data, letting you see information that organizations, companies, and website owners may not want you to see.
A simple example of an advanced search query is the use of quotation marks. Using quotation marks in searches gives you a list of results that includes web pages where the complete phrase is used, rather than some combination (complete or incomplete) of the individual words you entered into the search field.
There are many more types of Google hacks using advanced search queries, but their technical explanations don’t actually get much more complicated than that. Their power lies in the ability to use them creatively.
What is Google dorking used for?
Google dorking is used to find hidden information that is otherwise inaccessible through a normal Google search. Google dorks can reveal sensitive or private information about websites and the companies, organizations, and individuals that own and operate them.
In preparing for an attack, malicious hackers might use Google dorks to gather data on their targets. Google dorks are also used to find websites that have certain flaws, vulnerabilities, and sensitive information that can be exploited.
Security companies try dorking to better understand how someone might approach hacking into systems. Or, companies might use Google dorks to find information that can be leveraged in SEO and performance marketing strategies. Using Google hacks helps companies see exactly what kind of information others can find about them.
Along with information-gathering, dorking may grant access to servers, cameras, and files. Google dorks can be used to access all the webcams in a given area, they have even been used to access phone apps. Some dorking techniques have uncovered files of failed login attempts, including usernames and passwords. Other dorks have even let hackers bypass login portals.
 Google dorking can uncover all kinds of hidden information on Google.
Google dorking can uncover all kinds of hidden information on Google.
With dorks, there’s no Google hacking code to learn. Instead, hacking Google can be easily done through the use of simple search commands you can look up yourself. Worryingly, a combination of dorking and social engineering can reveal a lot of information that could be used to commit identity theft. That’s why it’s important to understand how Google database hacking works, so you can understand your own digital identity and strengthen your online security.
As the digital trail of your breadcrumbs widens every day, you’re more susceptible to online tracking, and more vulnerable to Google search hacks or other forms of computer hacking.
To help protect your personal data and improve your device security, you need a bulwark against the array of today’s online threats. AVG AntiVirus FREE provides award-winning online security to protect your digital life. Install it today for free.
Is Google dorking illegal?
Google dorking is completely legal — it’s just another form of searching after all. Google was built to handle advanced searches, and banning this functionality would limit information access.
But Google hacks can quickly become illegal if they’re used to surreptitiously access someone else’s device, log in to someone else’s account, or access or download protected files or documents. Searching for information may not be illegal, but using it for unauthorized purposes almost certainly is.
Google dorks: a historical background
Google dorks began in 2002 when the computer-security expert Johnny Long started using custom queries to search for elements of websites that he could leverage in cyberattacks. A form of penetration testing, Long called the custom search commands he used Google dorks, and the list of these queries grew into the Google Hacking Database. There, you can find all sorts of advanced queries that can be used to uncover various kinds of hidden information.
Though his tools have been used for unethical purposes, Johnny Long has devoted his infosec expertise to charity and international development, building infrastructure and technology training programs in underdeveloped countries.
Common Google dork operators and commands
For a better idea of how Google dorks work, here’s a list of some of the most common Google dorking commands. You may even find some of these useful in your daily search-engine life.
Consider this a Google dorking cheat sheet:
-
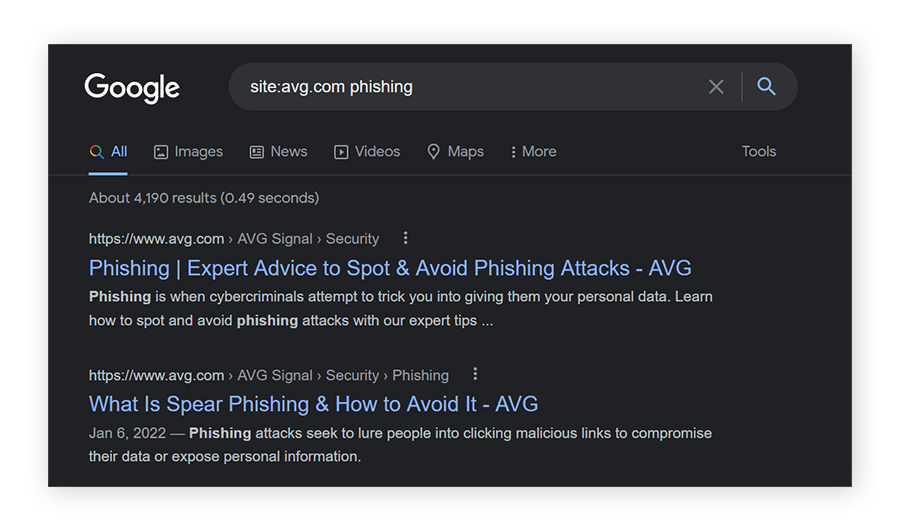
Site
Using “site:” in a search command will provide results only from the specific website mentioned.
-
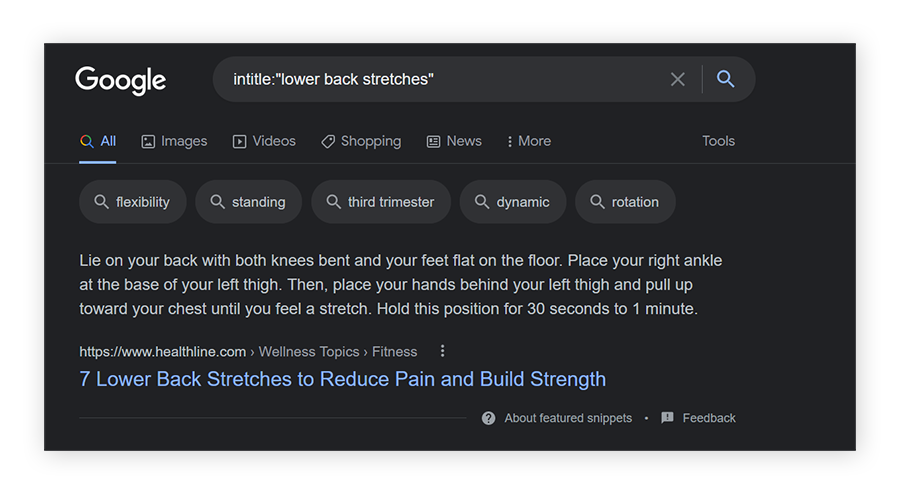
Intitle
Using “intitle:” asks Google to search only for pages with that specific text in their HTML pages titles.
-
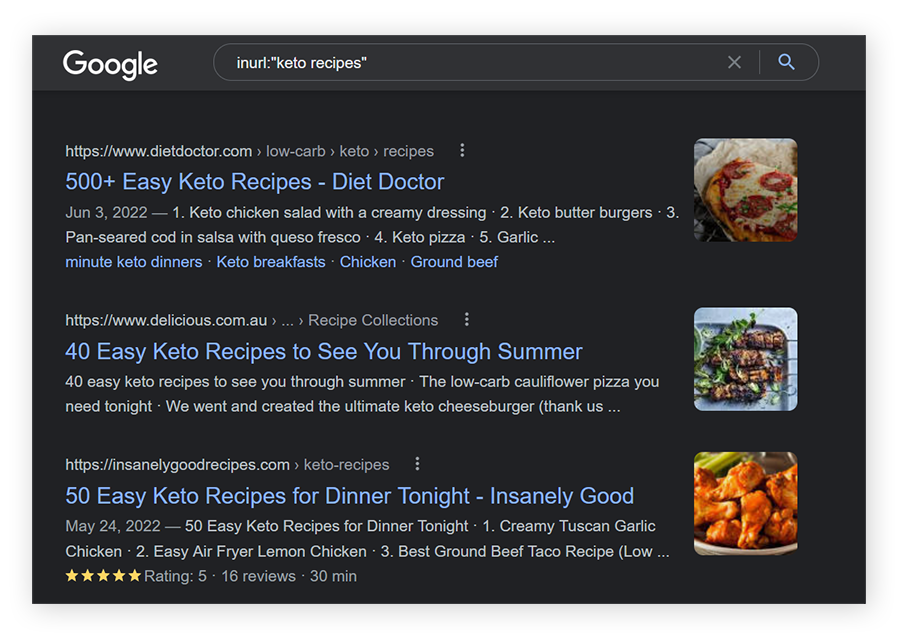
Inurl
Using “inurl:” will search only for pages with that specific text in their URL.
-
Filetype or ext
Using “filetype:” or “ext:” will narrow your search to the specific file type mentioned.
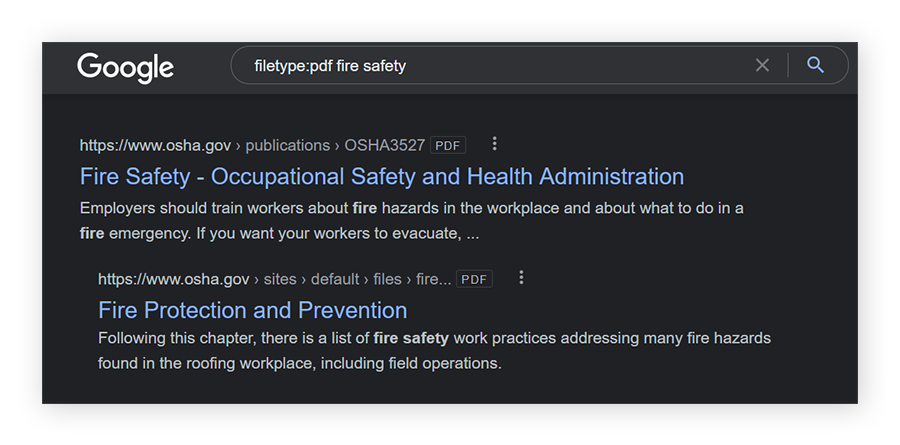
-
Intext
Using “intext:” in a search query will search only for the supplied keywords. In the example below, all results listed will have the quoted text somewhere on the page.
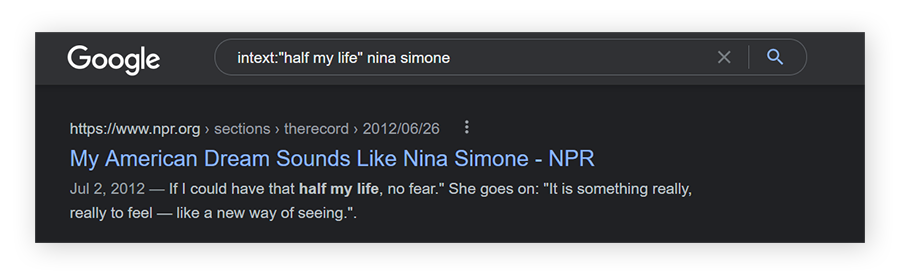
As shown in the example for “filetype” above, you can mix and match these Google dork commands depending on information you want to find. Make sure to use a colon after the type of dork you enter.
Advanced Google dork operators and commands
Now let’s examine more advanced Google hacking commands. Advanced Google hacks let you look up the archives of files, read recently-deleted content, and access CCTV webcams of certain areas like a parking lot or the grounds of a college campus.
Here are some examples of the more advanced ways to use Google dorking:
-
Cache
Using “cache” in your search can let you see older versions of a website or access files that have recently been removed. Try entering something like “cache:twitter.com/madonna” to see a history of the artist’s posts, including recently-deleted tweets.
-
:ftp
This advanced Google hack can be used at the end of a combined query to find FTP servers. FTP servers often hold large amounts of files. Search shakespeare:ftp to find a massive archive of all his texts.
-
Filetype:log
Using this Google dork will search for log files.
All of these can be combined with other keywords and operators for more precise searches. You can hone your search by adding additional parameters or commands and tightening the syntax you use. Dorks can also be automated to regularly scan for vulnerabilities and other information.
For more information on the complex syntax that can be used in Google hacks, go to the Google hacking database. As mentioned above, it is illegal to use Google dorks to access or download illegal or protected information.
How to protect against Google Dorking
Now that you know what kind of power Google dorks can hold, how do you protect against someone using information uncovered through Google dorking against you?
While it’s easy to become paranoid about how much data Google has about you and the danger that it could be hacked, worrying by itself won’t help. Instead, proactively strengthen your internet security to protect your personal data from the potential consequences of dorking, like a phishing attack.
Here are some of the best ways to protect yourself against Google dorking:
-
Use strong and unique passwords, and 2FA, for all your online accounts. That will greatly reduce the risk that someone breaks into your accounts with information uncovered through a Google hack. (And use a reliable password manager to store all your passwords.)
-
Run vulnerability scans. If you manage a website or other digital infrastructure, regularly run penetration tests to ensure any weaknesses are found.
-
Use Google Search Console to remove sensitive pages from public search results.
-
Run a Google dork on yourself to see what kind of personal information is visible.
-
If you’re a website admin, add robot.txt files to sensitive folders to tell Google not to index that content. Robot.txt is one Google antidote to malicious dorking.
-
Finally, install comprehensive security software, like AVG AntiVirus FREE, to protect your device and your personal data.
Control your digital footprint with AVG
With Google hoovering up so much of your personal data, maintaining internet security feels more daunting than ever. Thankfully, cybersecurity experts have taken up the task for you, developing strong apps and services to secure your digital life.
AVG AntiVirus FREE provides six powerful layers of online security protection, including anti-malware defenses, an email shield, and real-time updates to its virus definition database. Install AVG AntiVirus FREE today.

 Google dorking can uncover all kinds of hidden information on Google.
Google dorking can uncover all kinds of hidden information on Google.










