What is a Smurf attack?
A Smurf attack is a type of distributed denial of service attack (DDoS) that overwhelms a network with a high volume of requests. Smurf attacks send a flood of Internet Control Message Protocol (ICMP) requests to a targeted network to exploit IP vulnerabilities and significantly slow or shut down devices on the network.
DDoS attacks aim to shut down a network by bombarding it with spoofed IP data. In a Smurf attack, that data are ICMP echo requests, or pings. The attack uses devices connected to the network to create a botnet that overwhelms the network with a high volume of pings.
By taking down servers, Smurf attacks can result in significant revenue losses for a company. They can shut down services, disrupt website visitors, and lead customers to competitor websites. Smurf attacks can also be a cover-up for more serious threats, like data theft or intellectual property theft.
Why is it called a Smurf attack?
The Smurf attack is named after an exploit tool called Smurf that was popular in the 1990s. The ICMP packets created by the tool were small but took down big targets — similar to the characters in the popular cartoon “The Smurfs.”
How does a Smurf attack work?
A Smurf attack works similarly to a ping flood. Ping floods are also DDoS attacks that overload target networks with ICMP echo requests. The difference is that a Smurf attack does more damage by using all the devices connected to the targeted network.
Smurf attacks can orchestrate a multi-device attack by exploiting a flaw in a broadcast network. A hacker (host 1) uses a spoofed IP address to send an ICMP echo request (ping) to host 2, setting off an automatic response. The time it takes for the response to come back to host 1 measures the distance between the two hosts.
Then, when an ICMP echo request is sent to a broadcast network, it initiates a response from every IP address connected to the network. Like a computer security exploit, Smurf attacks take advantage of this vulnerability to maximize damage.
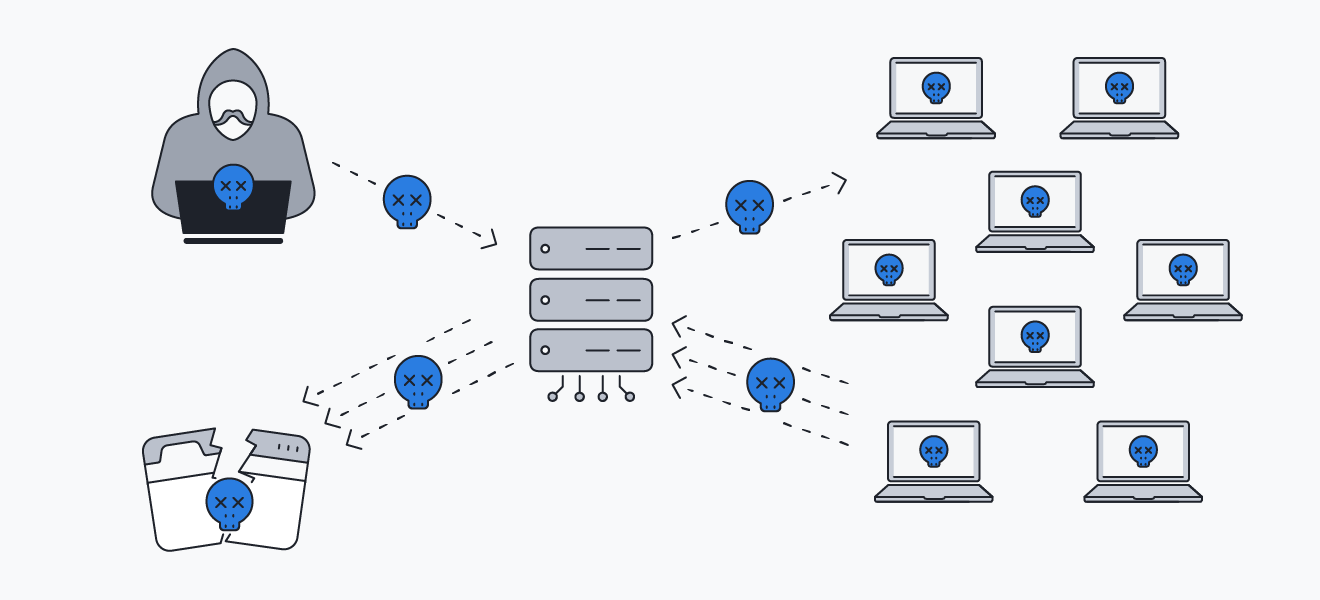 A Smurf attack is a type of DDoS attack that uses IP spoofing to take down networks.
A Smurf attack is a type of DDoS attack that uses IP spoofing to take down networks.
Here’s how a denial of service Smurf attack works:
1. Malware creates a network package
Using Smurf malware, the attacker creates an ICMP echo request that’s linked to a spoofed IP address. The fake IP is actually that of the target server. So when the echo request is returned, it will go to the target instead of the attacker.
2. ICMP ping messages are sent to the targeted IP address
The ICMP ping message is then sent to the targeted IP broadcast network, which relays the message to all the devices connected to the network. The devices that receive the data package are requested to send back a response to the spoofed IP address.
3. Continuous “echoes” bring down the network
The targeted server receives continuous replies from all the devices on the network, which are again sent back from the server. Called an “echo,” this infinite loop overwhelms a network and shuts it down indefinitely.
Smurf attacks try to remain disguised and undetected, and the long-term effect of accumulated echo requests is a slower network, which can leave connected websites and devices working painfully slowly or render them entirely inoperable.
If your internet is slow, but you don’t think it’s because of a DDoS Smurf attack, check out our guide to speeding up your computer. Your internet service provider could be the culprit — learn about ISP throttling and what you can do to stop it.
Signs of a Smurf attack
Smurf malware can remain dormant on a computer until an enterprising hacker decides to activate it. This makes it difficult to detect signs prior to an attack. But as a website owner or visitor, the most obvious sign of a Smurf attack is a very slow or inoperable server.
Although there are many reasons that can cause a network shutdown, it’s important to rule out a Smurf attack as well as any other malicious activity. A distributed denial of service Smurf attack could lead to more serious damage — like data theft or a ransomware attack.
If you suspect your computer is infected with malware, check out our guide to learn how to get rid of computer viruses.
What are the types of Smurf attacks?
Smurf attacks typically appear in two forms — through network driven DDoS attacks or by downloading Smurf malware. Familiarizing yourself with these differences can help you mitigate their potential damage.
Here are the types of Smurf attacks:
Basic Smurf attack
A basic Smurf DDoS attack bombards the targeted network with an infinite number of ICMP echo requests. These requests are relayed to all the devices connected to the server, which are prompted to send a response. The high volume of responses overwhelms the target server.
Advanced Smurf attack
An advanced smurfing attack starts as a basic one. The difference is that by configuring sources an advanced attack can respond to third-party victims. By expanding the attack vector, hackers can target larger groups of victims and more extensive networks.
Through downloaded software/applications
Smurf attacks can also be downloaded. In a trojan horse, Smurf malware can lie within software and application downloads, from unsafe websites or infected email links. If your device is infected with a trojan, use a trojan remover tool to remove it.
Smurf attacks can also be bundled in rootkits. This allows hackers to establish backdoors to gain unauthorized access to network data and systems. Rootkits can be tricky to spot, but a rootkit scanner can help you check for them.
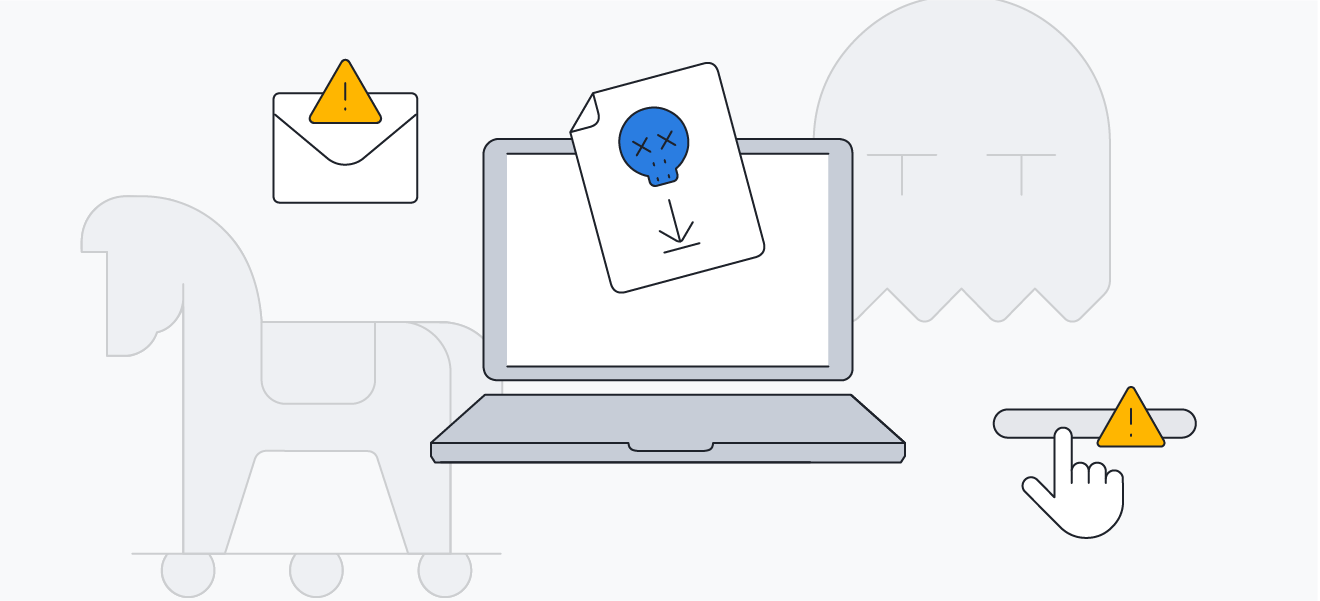 Smurf malware can also be delivered via trojans and rootkits.
Smurf malware can also be delivered via trojans and rootkits.
How to counteract or prevent a potential Smurf attack
Although an old technique, Smurf attacks are still effective. And because they are difficult to detect, Smurf attack prevention techniques are crucial for avoiding them.
Our guide to enhancing cybersecurity will help you understand general malware prevention techniques and good digital hygiene.
Here’s what you can do to prevent router hacking and steer clear of Smurf attacks:
-
Disable IP broadcasting: This feature sends data packets to all devices on a given network. It’s exactly what Smurf attacks rely on to increase their attack surface. Disable IP broadcasting on all network routers.
-
Configure hosts and routers: Smurf attacks weaponize ICMP echo requests. You can configure your hosts and routers to ignore these requests.
What is the difference between Smurf and fraggle attacks?
A fraggle attack is a variant of a Smurf attack. Where Smurf attacks send ICMP echo requests, fraggle attacks send UDP (User Datagram Protocol) requests. Smurf and fraggle attacks use different methods, but both target IP vulnerabilities to get similar results.
You can use the same prevention tips to avoid both Smurf and fraggle attacks.
Protect against Smurf attacks with AVG
In the online world, Smurf attacks are just one type of threat. For protection against the array of online threats out there, equip your device with powerful anti-malware protection like AVG AntiVirus FREE. Our antivirus engine provides six layers of protection to defend against DDoS attacks and the most advanced malware strains.
And with a built-in email shield, AVG AntVirus FREE also blocks dangerous attachments and phishing links that can put your data at risk. Install AVG today to get real-time threat protection.

 A Smurf attack is a type of DDoS attack that uses IP spoofing to take down networks.
A Smurf attack is a type of DDoS attack that uses IP spoofing to take down networks. Smurf malware can also be delivered via trojans and rootkits.
Smurf malware can also be delivered via trojans and rootkits.





