What is a security breach?
A security breach means unauthorized access to a device, facility, program, network, or data. It can involve the breach of security measures that protect data, network systems, or physical hardware assets, and it’s often the precursor to private data being copied, shared, or stolen in a data breach.
Types of security breaches
The types of security breaches vary according to the tools or methods attackers use to gain access to a restricted area — and whether it’s a digital or physical space.
Here are some common types of security breaches based on different methods of attack:
-
Malware: Malware is malicious software such as viruses, worms, ransomware, and spyware that’s designed to harm or gain unauthorized access to a system or device.
-
Social engineering: Social engineering is the use of deceptive tactics to trick victims into revealing personal or sensitive information. Social engineering attacks involve fraudsters masquerading as a person or organization the victim trusts. Phishing is a common tactic used, and the attacker may use spoofing as part of the scam to appear legit.
-
Physical security breaches: Physical security breaches occur when an attacker gains unauthorized access to an actual building or physical device. Social engineering ploys can be used in tandem — like a vishing attack — to trick insiders into divulging access to the building or device.
-
Ransomware: Ransomware is a form of malware that holds your files hostage by encrypting them and locking you out. In exchange for the decryption key, victims must pay a ransom to regain access.
-
DDoS attack: A distributed denial of service (DDoS) attack floods a website with traffic until it’s forced to shut down. This form of hacking can lead to a security breach because it overwhelms the security system of the target.
-
Man-in-the-middle attack: A man-in-the-middle attack occurs when an attacker intercepts and manipulates data as it travels between systems. Attackers can use this data for unauthorized access into targeted systems or devices.
 Cybercriminals use many tactics to access a device or network.
Cybercriminals use many tactics to access a device or network.
How does a security breach happen?
Here are some examples of how a security breach can happen:
-
Malware: The attacker infects a system with malware that’s designed to steal sensitive data, hijack system resources, or cause damage to the system. To help prevent this kind of intrusion, use anti-malware software to detect and remove threats from your system.
-
Phishing: This technique involves a seemingly legitimate email or text — in reality, it’s a scam — that includes a link to a fake website or login page. These links are designed to trick you into revealing sensitive data that will give the attacker access to an account like an online banking account.
-
Physical: These breaches could involve an attacker stealing or meddling with a piece of your equipment in order to gain access to your system or steal data. Another example is if someone steals a password that’s been written down — that’s why you should use a password manager to help you maintain the strongest passwords with ease.
-
Insider threats: These breaches are carried out by employees abusing their security clearance to access sensitive data. But they can also occur unintentionally by employees with weak passwords or ignorance of cybersecurity best practices.
Impact of a security breach
A security breach can have a severe impact on individuals and organizations — or not. It all depends on what the attacker does once they gain access. The more important the data, the worse the possible consequences of the security breach.
Here are some of the consequences of a security breach that can impact individuals and organizations:
-
Data loss: A security breach can result in the access and theft of sensitive data, including customer data. Malicious use of this data can lead to identity theft, financial fraud, or reputational damage.
 In a security breach, hackers can uncover a wide array of personal and business information.
In a security breach, hackers can uncover a wide array of personal and business information.
-
Financial damage: A breach of security can result in financial losses — especially if attackers gain unauthorized access to online accounts or financial documents. The aftermath can also result in expenses incurred from investigations, legal fees, customer notification and compensation, and possible fines.
-
Lawsuits: A security breach can result in legal consequences — especially for organizations that have compromised customer data. This can include fines, penalties, lawsuits, and regulatory scrutiny.
-
Reputational damage: Organizations that fall victim to a security breach may have trouble regaining the confidence of their customers or partners, meaning a possible loss of business opportunities and lasting reputational damage.
-
Operational damage: A security breach can disrupt normal business operations, meaning downtime, loss of productivity, and additional costs for recovery. Systems and networks that need to be taken offline can result in service disruptions that affect both customers and employees.
Examples of a security breach
In recent years, plenty of high-profile examples of security breaches have captured public attention, many leading to data breaches. In 2022 alone, data breaches, leakage, and exposure affected 422 million individuals in the US.
Cases like the Equifax hack prove that even trusted companies can fall victim to a data breach. And the most notorious physical security breach has to be the storming of the US Capitol building in January 2021.
Here are some other real-life examples of security breaches:
LastPass
In 2022, on the heels of a previous security breach, the password manager LastPass was hit with yet another security breach — by the same attacker. A company DevOps engineer’s computer was hacked and the attacker implanted keylogger malware.
The hacker was able to capture the engineer’s master password as it was entered and gain access to the customer vault data.
Yahoo
In 2013, Yahoo suffered one of the largest data breaches in history. Initially, the prominent web service provider reported that the hack stole user data from one billion accounts, but years later, the figure was amended to three billion accounts.
The security breach led to the theft of account information like names, email addresses, phone numbers, birthdates, and security questions and answers.
Uber
In 2022, a hacker gained access to the internal databases of Uber. Two theories exist on how: either the hacker bought the corporate password of Uber’s systems off the dark web, or they used social engineering tactics, posing as a corporate tech worker and tricking an Uber contractor into revealing the password.
The reported damages of this security breach were relatively minimal. But, in 2016, two hackers managed to access the names, email addresses, and phone numbers of 57 million users with the Uber app.
Facebook
In 2021, the stolen personal data of over 530 million Facebook users surfaced on an amateur hacking forum. The data was reported to have been from a 2019 data breach. Data stolen from the breach included phone numbers, full names, locations, email addresses, and other details from user profiles.
Somewhat controversially, Facebook decided not to contact the victims, so check if your details on Facebook were leaked. Facebook claimed that the data stolen did not include sensitive data like financial information, health information, or passwords. But cybersecurity experts warn that hackers can do a lot with very little data — especially phone numbers.
Security breach vs. data breach: What's the difference?
A security breach refers to unauthorized access to a system, data, device, or network; a data breach is when a cybercriminal steals data after breaking in. Though similar, a security breach is a broad term that includes different types of unauthorized access; while a data breach is a specific type of security breach.
A cybersecurity breach is not always malicious. Someone can accidentally gain access to a system due to weak security protocols or flaws in hardware or software. Whereas a data breach, by definition, is malicious as it’s the intentional access and theft of private data by an unauthorized entity.
How to prevent a security breach
It’s better to prevent a security breach than to resolve one after it occurs. Though not all security breaches are avoidable, applying a few tried-and-tested best practices can significantly decrease the chances you or your organization will be affected.
Here are some ways to prevent a security breach:
-
Secure your passwords: Create strong passwords that are unique for all of your accounts and change them regularly.
-
Two-factor authentication: Accounts that use two-factor authentication (2FA) require two or more forms of authentication for access, making them more secure.
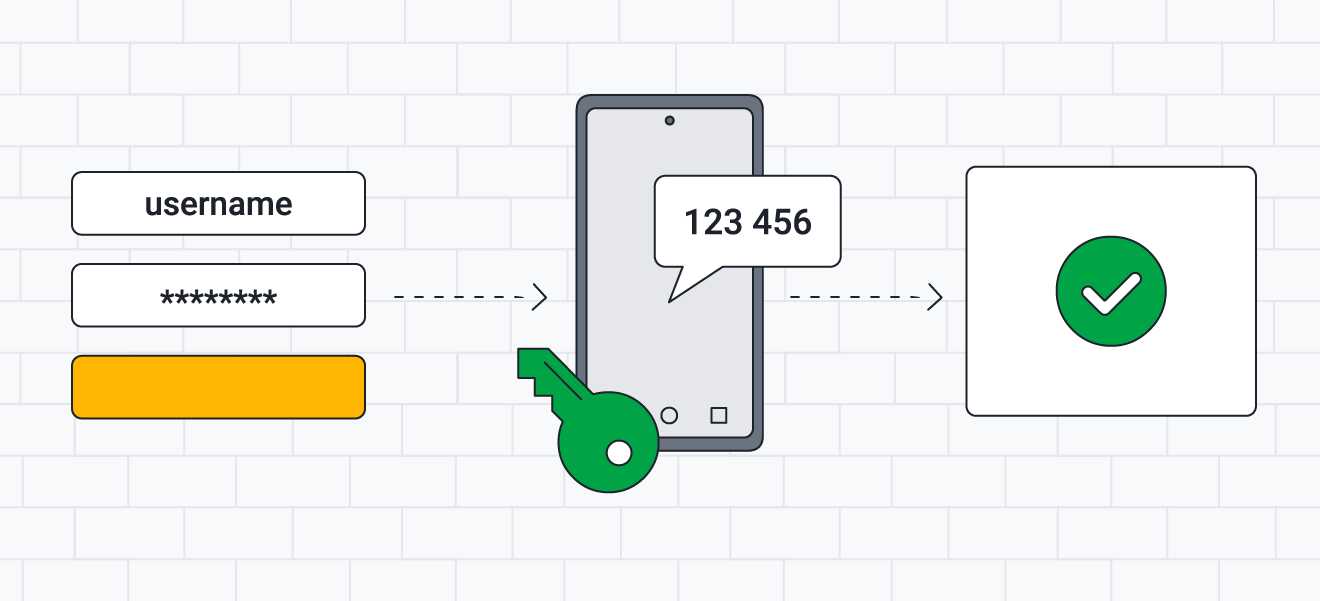 Use two-factor authentication to help protect your online accounts.
Use two-factor authentication to help protect your online accounts.
-
Regular software updates: Software updates often include fixes to security vulnerabilities. Regularly update your software and operating system to prevent hackers from taking advantage of these vulnerabilities.
-
Employee training: Like this Thomson data breach, many security breaches stem from human error. Though you can’t predict mistakes, you can increase cybersecurity awareness within your organization. Take the time to educate employees on large-scale cyber attack guidelines and how they can avoid possible threats.
-
Use anti-malware software: Quality anti-malware software can detect and remove threats to your system and devices long before you even ask yourself: “Have I been hacked?”
-
Security equipment: Offices and homes with valuable data and systems should protect against physical breaches by installing security equipment like cameras.
What to do if you experience a data breach
If you experience a data breach, here’s what to do:
-
Change your passwords: A security breach on one account could affect other accounts, so change the passwords for all of your accounts.
-
Run an anti-malware scan: A malware scan will target and remove malware resulting from a security breach.
-
Notify your bank and credit bureaus: Notifying your bank and freezing your credit with the credit bureaus will prevent the attackers from dipping into your finances.
If you fall victim to a data breach it’s crucial to act quickly. Depending on the severity of the breach, there could be lasting consequences for you, your organization, and others.
Protect yourself against security breaches
As the old security industry saying goes, “There are two types of companies: those who’ve been hacked, and those who don’t know they’ve been hacked.” Sometimes a security breach is inevitable, but you can help prevent further damage with AVG BreachGuard.
Our powerful cybersecurity tool provides 24/7 privacy risk monitoring to help keep your data from falling into the wrong hands. And in the event of a data breach, our online personal-info removal tool will help stop your data from being collected and exploited by third parties. Get AVG BreachGuard to help you protect your personal info and keep your online accounts secure.

 Cybercriminals use many tactics to access a device or network.
Cybercriminals use many tactics to access a device or network. In a security breach, hackers can uncover a wide array of personal and business information.
In a security breach, hackers can uncover a wide array of personal and business information. Use two-factor authentication to help protect your online accounts.
Use two-factor authentication to help protect your online accounts.




