What is a honeypot trap?
A honeypot trap is an intentionally compromised decoy system set up to lure hackers and other cybercriminals into a controlled environment to help cybersecurity professionals see how they operate. In computing, honeypots use fake networks and decoy data as bait to attract hackers. Cybersecurity experts then monitor the attacks to gain insights into how cyber attackers access and exploit online data.
By duping hackers into a honeypot, experts can identify threats, gather information on hacking methods, and develop more effective security policies and infrastructure. Honeypot traps have the added benefit of diverting hackers’ time and effort from trying to exploit real systems and networks.
Why are honeypots used in cybersecurity?
The main purpose of a honeypot in cybersecurity is to monitor and analyze attacks in order to improve protection against hacking attempts. A honeypot captures information from the hacker, which can be used to analyze the method of attack, see how the unauthorized intruder interacts with a network, and help cybersecurity professionals shore up vulnerabilities in their systems.
While the specific nature and purpose of honeypots vary, they generally fall within two main categories:
-
Production honeypots are used as an active defense by large organizations as a decoy, leading hackers away from the main network. Organizations use the data collected from this “controlled” hack to eliminate any weaknesses in their defenses and better protect their real network against hacking attempts.
-
Research honeypots are complex traps usually used by governments or large cybersecurity organizations to track the development of advanced persistent threats and stay on top of evolving hacking techniques.
How does a honeypot work?
A honeypot works by isolating decoy data or other digital assets within an intentionally compromised system or environment that’s separate from an organization’s real network. Cybersecurity specialists can then monitor all unauthorized traffic to the honeypot and learn about hackers’ tactics in a controlled environment while keeping the main network safe.
When setting up a honeypot, as well as dressing it up as low-hanging fruit that’s an irresistible target for different types of hackers, analysts also typically plant data that can be easily tracked, allowing them to monitor data breaches — often in real-time — and uncover connections between multiple participants in an attack.
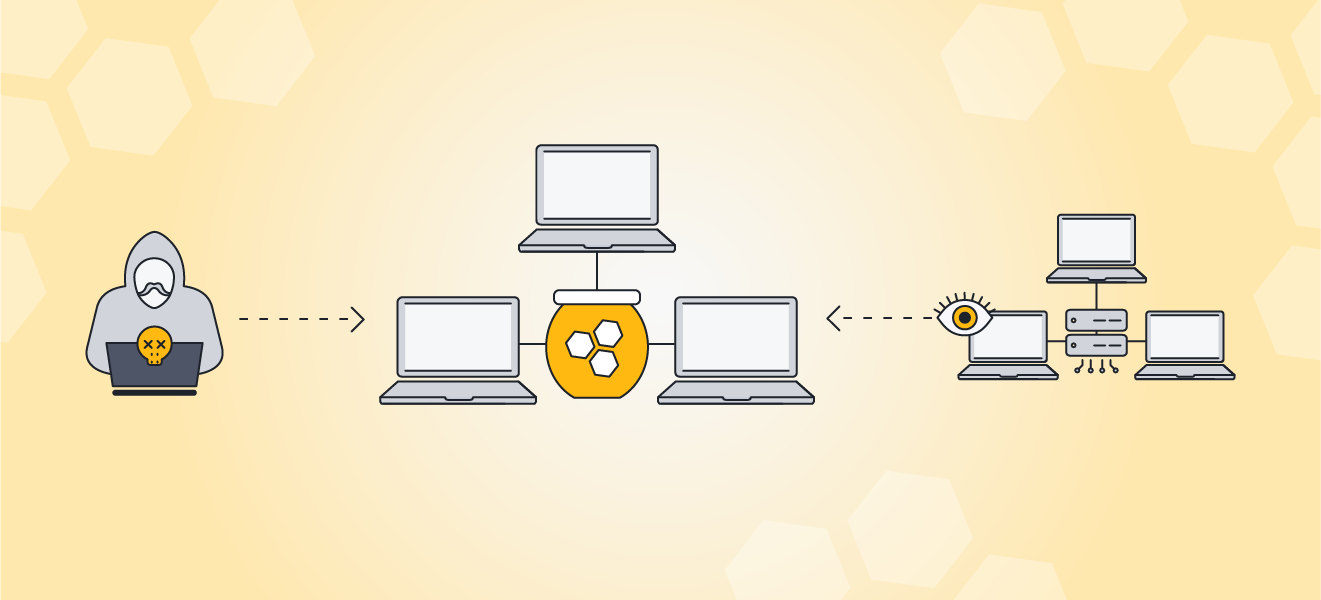 Honeypots entice and entrap hackers, helping to keep them away from real networks.
Honeypots entice and entrap hackers, helping to keep them away from real networks.
What is a honeynet?
A honeynet is a decoy network of honeypots. Whereas a honeypot is a single decoy device planted within a network, a honeynet is set up to look like a real network, often includes multiple servers or devices, and includes additional features such as firewalls. The intention behind a honeynet is similar to a honeypot — to analyze how hackers gain access and interact with the resources within it — but on a wider scale.
Honeypots by level of interaction
Honeynets and other forms of honeypot security can be further categorized according to three different levels of interaction:
-
Pure honeypots: comprehensive operational systems that are the most intricate and challenging to upkeep. Equipped with simulated sensitive documents and user data, pure honeypots present the most authentic appearance to potential intruders.
-
High-interaction honeypots: complex honeypots that allow hackers free rein within the infrastructure, offering analysts the most data about cybercriminals’ activities. High-interaction honeypots require more maintenance and can pose a higher risk.
-
Low-interaction honeypots: rather than imitating an entire system, these decoys represent the parts of a company’s systems and services that are most attractive to hackers. As such, they provide more limited information about the attackers, but can be more easily set up using TCP/IP protocols.
What are the different types of honeypots?
Different types of honeypots can be used to help explore and neutralize different types of threats. Here are some of the most common types of honeypots and how these different methods of honeypotting work in practice:
 Email honeypots
Email honeypots
Email honeypots use a spoofed email address that can only be detected using suspect methods such as an automated address harvester, meaning that no legitimate user can find the address. All messages sent to this address are therefore classified as spam, and the senders of these emails are immediately blocked from the network. This helps internet service providers to stop email spam.
 Data honeypots
Data honeypots
Organizations often create decoy databases with fake content to identify and eliminate system vulnerabilities. Data honeypots can gather information about SQL injections and other methods hackers use to gain access to the phony database, and they can also be used to analyze the spread and use of the fake data stolen in the attack.
 Malware honeypots
Malware honeypots
A malware honeypot is a technique intended to attract malware by mimicking a software app or API, creating a controlled environment where the creator can safely analyze a malware attack. This information can then be used to build more sophisticated defenses against malware.
 Spider honeypots
Spider honeypots
Web crawlers, or “spiders,” are the intended target of this type of honeypot trap. A spider honeypot creates web pages and links that can only be accessed by an automated web crawler or bot, giving organizations insight into how they operate and any potential problems they may cause.
 Client honeypots
Client honeypots
Conventional honeypots are server honeypots that passively await an attack. But client honeypots — or computer honeypots — are proactive security mechanisms seeking out servers that launch attacks. The client honeypot impersonates a client device, engages with the server, and investigates if an attack has taken place.
What are the advantages of using a honeypot?
There are many benefits of using a honeypot trap to ensnare would-be cyberthieves. Here are a few of the main use cases and advantages of operating a honeypot network:
Monitoring evolving threats
Cyber attacks are a constantly evolving threat to networks, and honeypots are one of the best tools available to keep an eye on the developing threat landscape. Once active, a honeypot continues to gather data each time it receives a hit, enabling network admins to identify patterns in the attacks (such as IP addresses in a particular location) and update their security measures to defend against similar activity.
Exposing vulnerabilities
Honeypots are invaluable for exposing vulnerabilities in organizations’ security in a low-risk manner. By analyzing which exploits attackers are using to access the data in the honeypot, organizations can update their security systems to help block these methods of attack.
Identifying insider threats
Honeypots can also be used to identify and catch internal threats before they can do any real damage. Internal threats from malicious insiders can be a major problem if there are weaknesses surrounding the permissions within the organization, giving disgruntled employees ways of exploiting the company’s data. But honeypots can preemptively identify internal weaknesses and threats just as effectively as external ones.
Low false-positive rate
Other types of technologies that identify security threats often have a high rate of false positives, where alerts flag nonexistent threats. But since honeypots cannot be accessed by legitimate means, there’s a very low rate of false positives.
Cost-effective
Since they are relatively low maintenance, and security teams don’t need to sift through large amounts of data searching for suspicious activity, honeypot technology is a cost-effective defense against online attacks. They have limited traffic and don’t have high server demands — especially in low-interaction systems. Honeypot software is also often open source, making it cheap and easy to implement.
Essential training tool
Cybersecurity staff can use honeypots as a cutting-edge training tool by analyzing the data gathered about online attacks. Honeypots are unparalleled in their ability to allow security personnel to remain up-to-date on new and evolving online threats.
 Honeypots are a valuable cybersecurity training aid against a wide range of threats.
Honeypots are a valuable cybersecurity training aid against a wide range of threats.
What are the risks of using a honeypot
Despite their many uses, honeypots are not a silver bullet when it comes to cybersecurity, and they do have several disadvantages. Here are a few of the limitations and drawbacks of using a honeypot:
Potential hijacking
While honeypots are usually isolated from an organization’s main network, there is a risk that a hacker may be able to use the honeypot as a lateral gateway to access and attack an organization’s real systems. Alternatively, if a sophisticated, dangerous hacker can identify, or “fingerprint,” a honeypot using a honeypot detector, they could flip the ruse by launching fake attacks on the decoy system to distract from a real hacking attempt elsewhere.
Limited data
Because honeypots can only gather data from attempted attacks, there will be limited data to analyze if the honeypot fails to attract potential threats. Relying too heavily on the data gathered by a honeypot can be a risk in itself, as experienced hackers and more complex threats may be overlooked if an organization’s security team is focused only on the risks identified via the honeypot.
Are honeypots illegal?
Honeypots are not illegal, but there are legal issues around the gathering of personal data of users. In the U.S. there’s a broad exemption to federal privacy law referred to as the service provider protection exemption, which generally allows organizations to collect information on users in the context of protecting and securing their network.
Other major pieces of legislation that govern the use of honeypots include the Electronic Communications Privacy Act in the U.S. and the E.U.’s General Data Protection Regulation (GDPR).
Any organization that wants to use a website honeypot or another form of cyber trap should first check the privacy legislation in their specific jurisdiction to ensure that their use of a honeypot does not violate any laws or regulations.
Get ironclad protection with AVG
Honeypots are an important piece in the cybersecurity puzzle. But most of us don’t have the resources to set up honeypots at home. That’s where reliable anti-malware software comes in.
AVG AntiVirus FREE uses advanced AI-enabled heuristic threat detection to help shield your device from viruses and malware, defend against emerging threats, alert you to unsafe links and websites, and block hacking attempts. Get cutting-edge protection today.

 Honeypots entice and entrap hackers, helping to keep them away from real networks.
Honeypots entice and entrap hackers, helping to keep them away from real networks. Honeypots are a valuable cybersecurity training aid against a wide range of threats.
Honeypots are a valuable cybersecurity training aid against a wide range of threats.




