Why is wireless security important?
Wireless security is important because network vulnerabilities can expose unsecured data that can then be stolen and used against you. Even if your computer has strong protection, other devices connected to your wireless network might still be compromised if the network itself isn’t secure.
Your internet router isn’t just the place where you can boost your home’s Wi-Fi strength. It’s a critical security hub, too. And if there are vulnerabilities in your router, your DNS settings could be hijacked, among other problems, and you could end up unknowingly visiting fake or dangerous websites.
Public Wi-Fi networks (like those in restaurants and cafes) can leave you exposed, too. Without strong security protocols, you can accidentally leave passwords and even online payment information available for someone on the same network who’s snooping for personal details.
Unless you’ve got the best wireless security, any device online can be hacked. Thankfully, encryption standards have improved over the years, minimizing vulnerabilities and neutralizing threats. The best Wi-Fi security protocol will prevent router hacking and help you browse safely on public Wi-Fi.
Let’s take a look at the different Wi-Fi security types implemented over the years.
Types of Wi-Fi security protocols
The most common wireless security protocol types today are WEP, WPA, and WPA2. Each protocol uses a different kind of encryption to strengthen network security. The most recent protocols, including the newest WPA3 protocol, have proved very robust, with workarounds much harder for hackers to pull off.
Wired Equivalent Privacy (WEP)
Wired Equivalent Privacy (WEP) used to be the standard form of encryption, but it’s no longer secure, because computing power has improved and hackers can now crack it easily. WEP security encrypts with a static key — one of the biggest reasons it’s no longer considered secure.
Introduced in 1997, WEP uses a single key to ensure the security of an entire network. If one user is compromised, everyone on the network is. When WEP security was introduced, the 64- or 128-bit string was difficult to crack, creating a formidable wall between a user network and hackers trying to intercept wireless signals.
Now, it’s a trivial matter for even a consumer-grade computer to run the calculations needed to decrypt a WEP key. The WEP security protocol was retired in 2004, so systems still using it should be updated.
 Pros
Pros
-
Most devices recognize WEP, meaning it was simple to set up and use.
-
It aimed to equal the security benefits of wired internet connections.
-
When it was introduced, the encryption algorithm was complex enough to keep unfamiliar users out.
-
WEP protected against man-in-the-middle attacks.
 Cons
Cons
-
Used a static encryption key, which had to be changed manually and updated on each individual machine to ensure the security benefits of later protocols.
-
Part of the key was transmitted as easily decipherable plaintext.
-
Too many security holes have been discovered over the years.
Wi-Fi Protected Access (WPA)
WPA (Wi-Fi Protected Access) security was designed to address many of the problems that emerged with WEP. Becoming the standard in 2003, WPA encrypts the network access key dynamically, by changing it regularly with TKIP (Temporal Key Integrity Protocol). That way, hackers can no longer crack the key by collecting transmitted data over a long period of time.
TKIP created a dynamic security environment, but it still wasn’t enough. Security experts quickly discovered that TKIP could be cracked with even small amounts of data.
As a result, a replacement cipher (or encryption algorithm) to WEP and WPA’s RC4 cipher was crowdsourced to cryptographers around the world, with the Belgian-made AES cipher proving to be the most secure during the competitive selection process. AES found widespread adoption with WPA’s successor, WPA2, which we’ll discuss in the next section.
 Pros
Pros
-
Introduced TKIP, or dynamic key encryption, which regularly changes the network access key.
-
All devices on the network recognize the new key when it’s generated.
-
Increased the complexity of security keys and their authentication.
 Cons
Cons
-
TKIP has proved vulnerable and can be easily hacked.
-
The complexity of the algorithm can now be overcome by modern processing power.
-
Unless users and network admins created strong passwords, data was vulnerable.
-
Comparing WPA vs WEP, the security benefits of WPA were significant — but WPA’s own flaws quickly became apparent.
Wi-Fi Protected Access II (WPA2)
The WPA2 security protocol increased the complexity of its predecessor (WPA) and has been the standard for network security for over a decade. It uses the AES cipher, an encryption process that would take billions of years for even an advanced computer to break.
But WPA2 also has its security flaws. A KRACK attack can gain access during the “handshake” — the moment a network authenticates a device connection — leaving a victim’s passwords and other data vulnerable to interception. To pull off such an attack, the hacker must be in close proximity to the network, which isn’t ideal for even the best hackers.
The significant security differences between WPA and WPA2 has made the WPA2 protocol last longer than any previous security protocol.
 Pros
Pros
-
Carries the same advantages introduced with WPA.
-
Usually uses AES encryption, an extremely robust cipher.
-
Requires passwords to be longer, adding extra security.
 Cons
Cons
-
Requires a greater amount of processing power (now negligible with current technology).
-
Can be vulnerable to man-in-the-middle attacks.
-
After over a decade since being introduced, a crack was finally discovered.
What about the WPA3 protocol?
WPA3 was introduced in 2018, and became a standard security protocol in 2020, but it may take a while before widespread adoption occurs. Most homes and businesses still use WPA2, and WPA3-compatible hardware can be costly. With WPA3, encryption between a user’s device and the network is specific and individualized, and users won’t even need to enter a password.
Under WPA2, a device and its data can be compromised once a hacker breaks through the network’s encryption. That will no longer be possible with WPA3, because of the added layer of individualized encryption.
WPA3 also addresses the security flaw in WPA2 that allows for KRACK attacks. And the encryption algorithm is much more complex — so complex that modern computers would need billions of years of calculations to get into just one network secured by WPA3.
WPA vs WPA2
Let’s summarize the differences between WPA and WPA2.
| |
WPA
|
WPA2
|
|
Date introduced
|
2003
|
2004
|
|
Best available
encryption method
|
TKIP, an imperfect system
that can be cracked
|
AES, the most secure
encryption widely
available
|
|
Password length
|
Minimum length is very short,
compromising security
|
Minimum length is long,
strengthening security
|
|
Home vs Business
options
|
Home only
|
Enterprise option
|
|
Processing power
required
|
Very little
|
More than WPA,
but negligible by today’s
standards
|
|
Date of security
flaw discovery
|
2008
|
2018
|
Today, WPA2 remains the standard protocol for Wi-Fi security, especially due to its strong AES encryption method.
WEP vs WPA vs WPA2
WPA2 is the best security protocol option widely available today, and we’ll all continue to use WPA2 passwords at homes and cafes for several years. WPA2 uses a dynamic network access key and multiple layers of protection for any network it’s protecting. Meanwhile, the older WEP standard has a static key that’s easily crackable.
Of all the Wi-Fi security types, WPA2 would take the longest to crack. And this exploit is still only theoretical — it hasn’t yet been seen in the real world. WEP and WPA protocols have been shown to be crackable in minutes, and neither homes nor businesses should use them.
WEP, WPA or WPA2 — which Wi-Fi security protocol is the best for my router?
The best Wi-Fi security option for your router is WPA2-AES. You might see WPA2-TKIP as an option, but it’s not as secure. WPA2-TKIP is, however, the second-most secure — followed by WPA, and then WEP.
WPA3 will soon become the most secure option — once it’s widely adopted — and you should switch to that protocol when it’s available.
Here are the security standards ranked from best to worst. Follow the right security recommendation, and Wi-Fi in your house or business will remain as secure as possible.
Even some security is better than no security, so make sure to implement one of these options, even if the best one isn’t available to you. Stick with a long, complex password and change it regularly to keep a WEP or WPA connection a little more secure than it would be otherwise.
If you’re looking to buy a new router or connect to the internet with a new provider, see if you can get a Wi-Fi certified WPA3-ready router. There’s no transitional period or incompatibility issues to worry about — you’ll be all set to use the most capable and secure option once WPA3 is available for your network.
Hopefully, that invaluable little box will do what it should and removing router viruses will become a thing of the past. And perhaps none of us will ever need to worry about how to fix Wi-Fi that isn’t working ever again.
How can I find my current Wi-Fi security protocol?
Here’s how to find which Wi-Fi security protocol you’re using:
-
Click the Windows Start menu and select Settings (the gear icon).
-
Select Network & Internet.
-
Choose Wi-Fi in the left panel.
-
Click the name of the wireless network you’re connected to.
-
Next to Security type you’ll see the wireless network protocol you’re using.
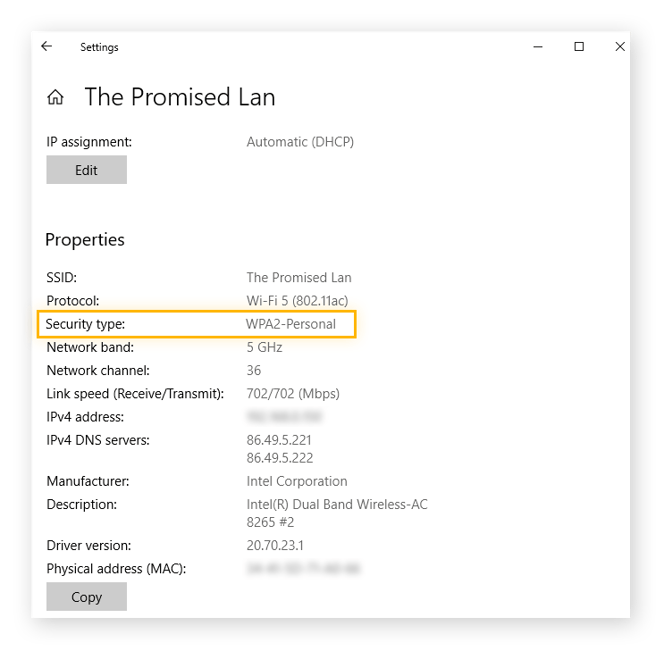
If you’re using WPA2 vs WPA3, but want to switch to WPA3, you first need to ensure that the Protocol field in your Wi-Fi network settings says Wi-Fi 6.
Protect your Wi-Fi network with AVG AntiVirus FREE
Wireless security has improved a lot over the years. But where your network security still falls short, dedicated antivirus software provides an extra line of defense.
Home network security is essential, and AVG AntiVirus FREE will help you fill any security gaps. AVG stops viruses, ransomware, and other malware with six powerful layers of protection. And it updates 24/7, meaning your device gets real-time protection from the vast array of cybersecurity threats. Whether you’ve made the switch to WPA3 or not, add AVG to your home security arsenal.







