What is Cobalt Strike?
Cobalt Strike is commercially available penetration testing or threat emulation software originally developed for the security community to simulate cyberattacks and uncover vulnerabilities. While organizations use Cobalt Strike to avoid malware, cybercriminals regularly steal and exploit it as a real hacking tool.
A key part of Cobalt Strike is the Beacon, a piece of software injected into the target computer to create a secret communication channel that enables the Cobalt Strike server (controlled by the hacker) to send commands to the Beacon. Possible commands include logging keystrokes, hacking your webcam, and installing ransomware or other malware onto your computer. The Beacon, in turn, can transmit stolen data back to the server.
The Cobalt Strike Beacon can also conduct reconnaissance, meaning it scans the target to identify the type and version of software being used. The purpose of this is to find any software with vulnerabilities that can be easily exploited — very handy for different types of hackers trying to gain unauthorized access to a system.
These features of Cobalt Strike allow organizations to simulate a hacker secretly operating in their network over a long period — known as an Advanced Persistent Threat (APT). By finding out what types of attacks could potentially be carried out by this “quiet” actor, the organization discovers which parts of its network need strengthening.
A main difference between Cobalt Strike vs. Metasploit, another threat emulation tool, is that you need to purchase a license from Cobalt Strike’s developer, HelpSystems, while Metasploit is free, open-source software.
How is Cobalt Strike used by hackers?
Sophisticated hackers have found ways to crack the Cobalt Strike license key and use it to target and infiltrate computers — under the guise of legitimate software — to steal money and data. Once a cybercriminal installs Cobalt Strike on a target device, it can assess vulnerabilities, unload ransomware, and execute other commands via the Beacon’s secret communication channel.
Here’s a step-by-step breakdown of how hackers use Cobalt Strike to search for specific vulnerabilities to exploit:
-
A hacker purchases or steals leaked, modified, or cracked Cobalt Strike software.
-
The hacker initiates a Cobalt Strike download by tricking the target into clicking a phishing link, or via a range of other hacking techniques.
-
Once installed, the hackers initiate Beacon to search for and identify vulnerabilities on the target’s computer.
-
Once an attack vector is discovered, the Cobalt Strike Beacon is used to gain remote access to the device and download ransomware or other malware.
-
The Beacon covertly sends back stolen data to the Cobalt Strike server.
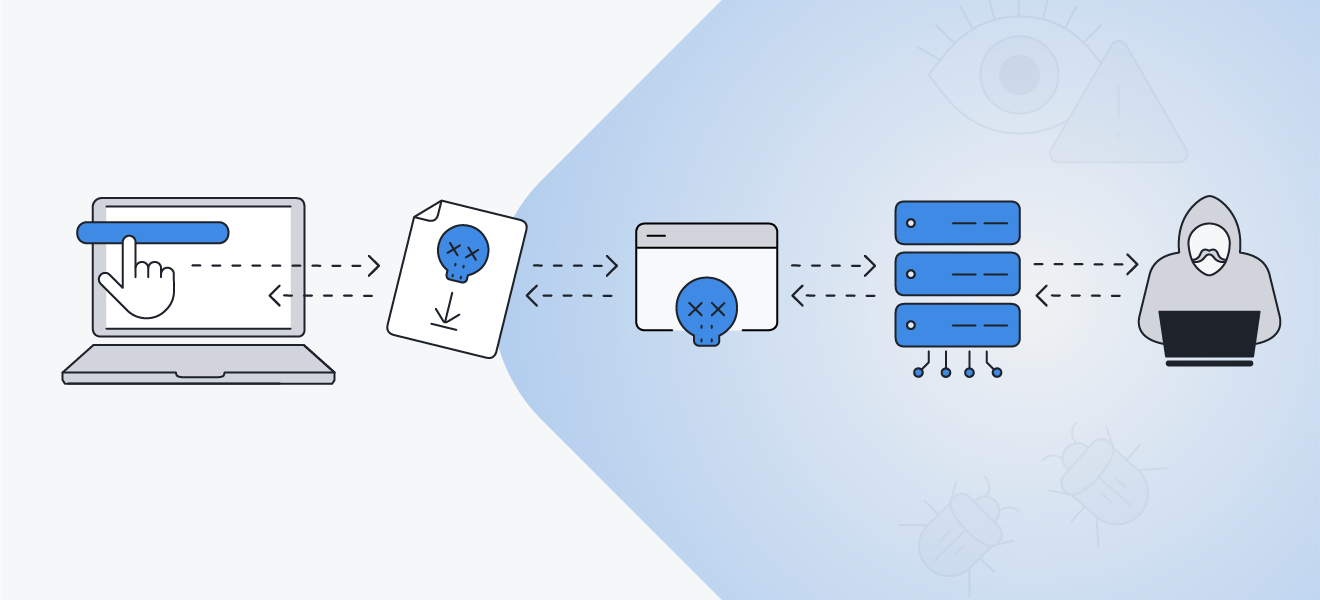 Hackers use Cobalt Strike to gain remote device access to install malware and steal data.
Hackers use Cobalt Strike to gain remote device access to install malware and steal data.
Who is at risk of a Cobalt Strike attack?
Anyone can be at risk of a Cobalt Strike attack, but hackers tend to focus on wealthy individuals or large organizations using spear phishing tactics. This is because malware delivered via the Cobalt Strike Beacon — also known as Cobalt Strike ransomware, Cobalt Strike malware, or Beacon malware — is usually used to extract money or steal data.
Thankfully, there are ways of protecting yourself from Cobalt Strike attacks, most notably keeping all of your software updated to reduce vulnerabilities.
How to identify Cobalt Strike on your network
What makes Cobalt Strike-based attacks so nefarious is that they're difficult to detect, even by experts. While cybersecurity experts may be able to use complex analysis to detect Cobalt Strike on your network, the average person probably wouldn’t be able to tell that the Cobalt Strike Beacon has infected their system.
That being said, you should always be on the lookout for signs that your computer has been hacked, including messages from fake antivirus software, unusual network traffic patterns, and unknown browser toolbars. At the end of the day, however, your best bet is stopping hackers from getting into your network in the first place.
How to avoid installing malware
As is usually the case in cybersecurity, prevention is the best medicine. Whether malware comes from Cobalt Strike or another source, here are some actions you can take to avoid installing malware on your computer:
-
Use strong antivirus software. Get ransomware protection or a malware and virus removal tool to help identify and remove malware, and help prevent new threats from infecting your device.
-
Keep your device up to date. Always update your drivers and software to help patch known vulnerabilities.
-
Use additional verification. Add a second layer of protection to your passwords with two-factor authentication to make it harder for hackers to break into your accounts.
-
Trust your instincts. When something feels “off” in an email, such as a strange email address, odd spelling or formatting, or a request to click a link or download a zip file, trust your gut as it could be a phishing attempt.
-
Use an automatic ad-blocker. Malware can come hidden in ads, known as malvertising. The easiest way to steer clear of this threat is to block ads with an ad-blocker or a browser with a built-in ad-blocker.
-
Do not pay the ransom. Ransomware can cost you a lot if you pay the ransom, but paying up is no guarantee the hacker will release your files or remove any other harmful code they’ve implanted.
Identify ransomware threats early with AVG
No matter how careful you are, crafty hackers can still slip malware through the cracks. But you can rest easy with round-the-clock protection from AVG AntiVirus FREE.
Our powerful security software provides real-time updates and six layers of security to help detect and block viruses, malware, and ransomware before they become a problem. Help secure your devices today — completely free.

 Hackers use Cobalt Strike to gain remote device access to install malware and steal data.
Hackers use Cobalt Strike to gain remote device access to install malware and steal data.





