What is spear phishing?
Spear phishing is a targeted type of phishing attack that involves sending an email or other electronic message to a specific individual, organization, or business to try to get them to reveal private information. The message is specially crafted to appear authentic and come from a trusted source, which makes spear phishing attacks especially dangerous.
How does spear phishing work?
A spear phishing attack begins with an attacker identifying a specific target and researching personal details, such as their employer, friends, hometown, recent online purchases, etc. The personal info gathered helps the attacker disguise themselves and create an authentic-looking message that appears to come from a trusted source, like an employer, friend, or well-known company.
Why is spear phishing effective?
Spear phishing is an especially effective type of phishing attack, because victims are specifically targeted and the messages that hook them are designed to appear quite authentic. Even the best cybersecurity protocols won’t keep emails from known contacts at bay. You may think that spotting a spear phishing attack would be easy, but you’d be surprised at how convincing these messages can be.
Social engineering tactics play an outsize role in spear phishing’s efficacy. The most successful spear phishing attacks involve messages that appear so authentic that it’s easy for a victim to fall for the ruse. Design elements in the message may look extremely authentic, and the email address the attacker uses may actually be a real address — the attacker might have committed identity theft and used another victim’s email address to launch a spear phishing attack.
A common spear phishing example is when an apparently normal message appears to come from the email account of an employee — or even the CEO — of a known company. Sometimes the harmless-looking message may be disguised as a notification from a well-known app like Microsoft Teams or Google. In each case, a potential victim is specifically addressed and personal information is included in the message.
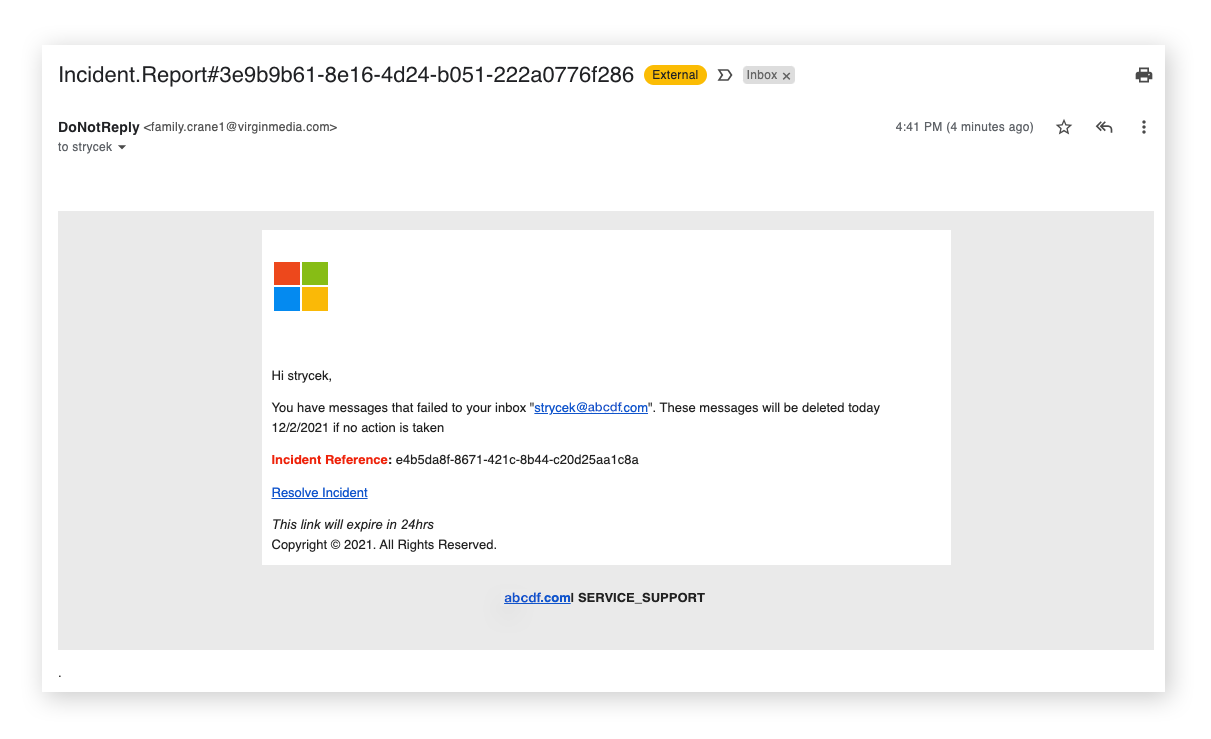
From there, the spear phishing attack works like a regular phishing attack. A malicious link or attachment is included in the message, and the sender often uses urgent phrases like “please review immediately” or “your account will be deleted if you don’t act now.” This urgency leads victims to focus on the request or notification itself rather than illegitimacy of the appeal.
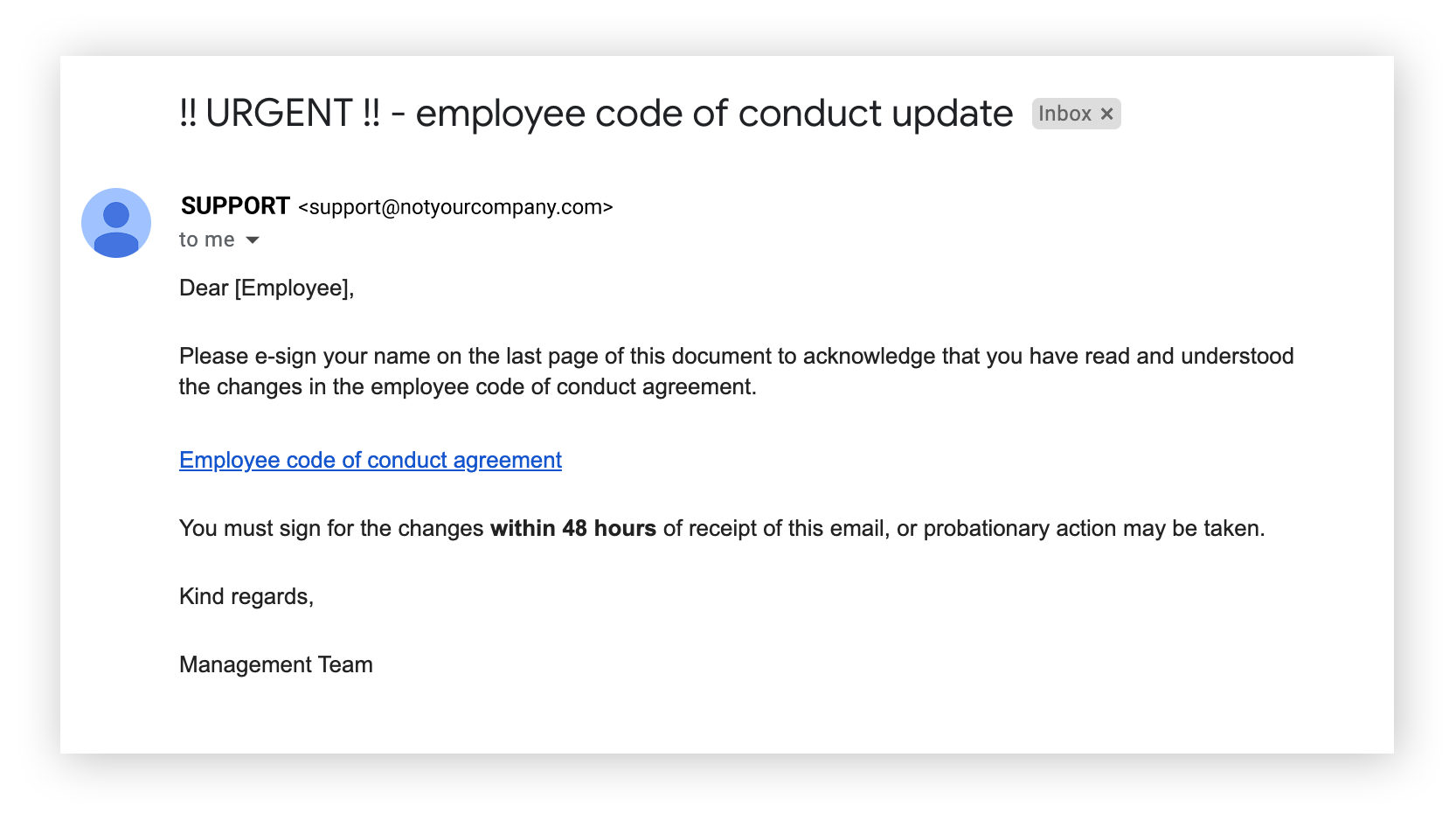
It’s unclear how many individuals or businesses are targeted by spear phishing attacks every day. According to one report, 88% of businesses faced spear phishing attacks in 2019, with the majority of respondents reporting more than 10 attacks that year.
Spear phishing examples
Spear phishing impacts large and small companies alike, and well-known individuals have also been targets. No one is safe from a spear phishing attack — not even Twitter employees or Jeff Bezos.
Facebook and Google
One of the biggest spear phishing attacks on record targeted two of the biggest tech companies in the world: Facebook and Google. The attacker impersonated an employee from Quanta, a Taiwanese tech company that both companies use as a vendor, and issued fake invoices to their financial departments, which Facebook and Google eventually paid.
The attacker stole $100 million before the scam was discovered. Thanks to the tech companies’ vast resources, they were able to find and prosecute the attacker, recovering nearly half of the stolen funds.
Ubiquiti Networks
In 2015, computer networking company Ubiquiti Networks was scammed out of $46.7 million through a spear phishing attack. The attackers targeted the company’s financial department, posing as employees and making fraudulent requests. While the company was able to recover some of the stolen money, much of it was lost for good.
Twitter
In 2020, several famous Twitter users — such as Jeff Bezos, Elon Musk, and Kanye West — had their Twitter accounts hacked as a result of a spear phishing scam. The hackers posed as IT workers in order to trick Twitter employees into giving them security credentials for an internal company tool, which allowed them to reset passwords and two-factor authentication for over 45 accounts.
The hackers then used these compromised accounts to tweet messages promoting a Bitcoin scam, in which followers were promised to receive double the amount of Bitcoin that they sent to a certain account. Because the tweets came from verified Twitter accounts and famous names, the scam successfully bilked several people out of Bitcoin.
Epsilon
In 2011, Australian email service provider Epsilon was the victim of a spear phishing attack. The fishy emails targeted employees handling email operations, and it led to the attackers accessing hundreds of client email addresses and compromising the company’s security systems. Several more spear phishing attacks followed, targeting dozens of Epsilon clients.
Google Drive collaboration scam
In 2020, a new spear phishing scam hit Google, this time targeting individual users rather than the company itself. This scam exploited Google Drive’s collaboration feature, in which Google sends users an email notifying them that someone wants them to collaborate on a project. Wired magazine was even targeted, receiving a Google collaboration notification linked to a fraudulent Russian email account.
What is the difference between phishing and spear phishing?
The difference between a phishing and spear phishing attack is that while a phishing attack casts a wide net, attempting to lure many victims at once, spear phishing targets specific individuals or companies. Both types of attacks use messages that appear to come from legitimate sources, thereby convincing victims that the messages are genuine and trustworthy.
Phishing attack emails include broader, less specific messaging — they’re targeting lots of people, so the messages need to be crafted more generally. Only a small percentage of targeted victims need to respond for the phishing attack to be successful.
Spear phishing attacks apply the same principle, but target a particular person or group. Attackers research victims for information to use and compose their emails and messages carefully. While both phishing and spear phishing attacks are often launched from apparently authentic email addresses, the information included in spear phishing messages is usually much more personal, focused on the specific target.

Other types of phishing
Other types of phishing attacks are out there, each taking a slightly different approach from the classic phishing scam.
-
Angler phishing uses social media posts, direct messages, and notifications to lure victims.
-
Whaling happens when a company’s CEO is impersonated, which heightens the legitimacy and urgency of the attack.
-
Barrel phishing, also known as double-barrel phishing, targets specific individuals in a two-stage attack process. First, a benign message is sent to gain the victim's trust. Then the real attack begins with a message that includes a malicious link or attachment.
-
Vishing, or voice phishing, occurs over the phone rather than through email. The attacker impersonates an authority, such as the IRS, and urges the victim to pass over sensitive details like their social security number.
-
Smishing refers to phishing attacks that happen through sms or text messages.
-
Pharming refers to attacks that redirect users to malicious websites set up via a process known as DNS hijacking. Pharming attacks work by luring victims to fake websites that otherwise look legitimate.
-
Evil twin phishing (also known as an evil twin attack) happens when hackers set up fake Wi-Fi networks that appear legitimate and encourage victims to log in with their real credentials.
-
Catfishing refers to creating a fictional identity or persona on social media to gain a victim’s trust. Catfishing tactics are usually used to trick victims for financial gain.
How to prevent spear phishing attacks
The best way to protect yourself against spear phishing attacks is to educate yourself on cybersecurity basics, like how to spot a suspicious email and what to do when you get one.
Suspicious emails may have grammatical mistakes that native speakers wouldn’t make, typos that suggest carelessness, requests for sensitive information (which legitimate companies never do via email), or unsolicited attachments. Links or attachments in spear phishing emails often appear legitimate, because they seem to be coming from a known and trusted source.
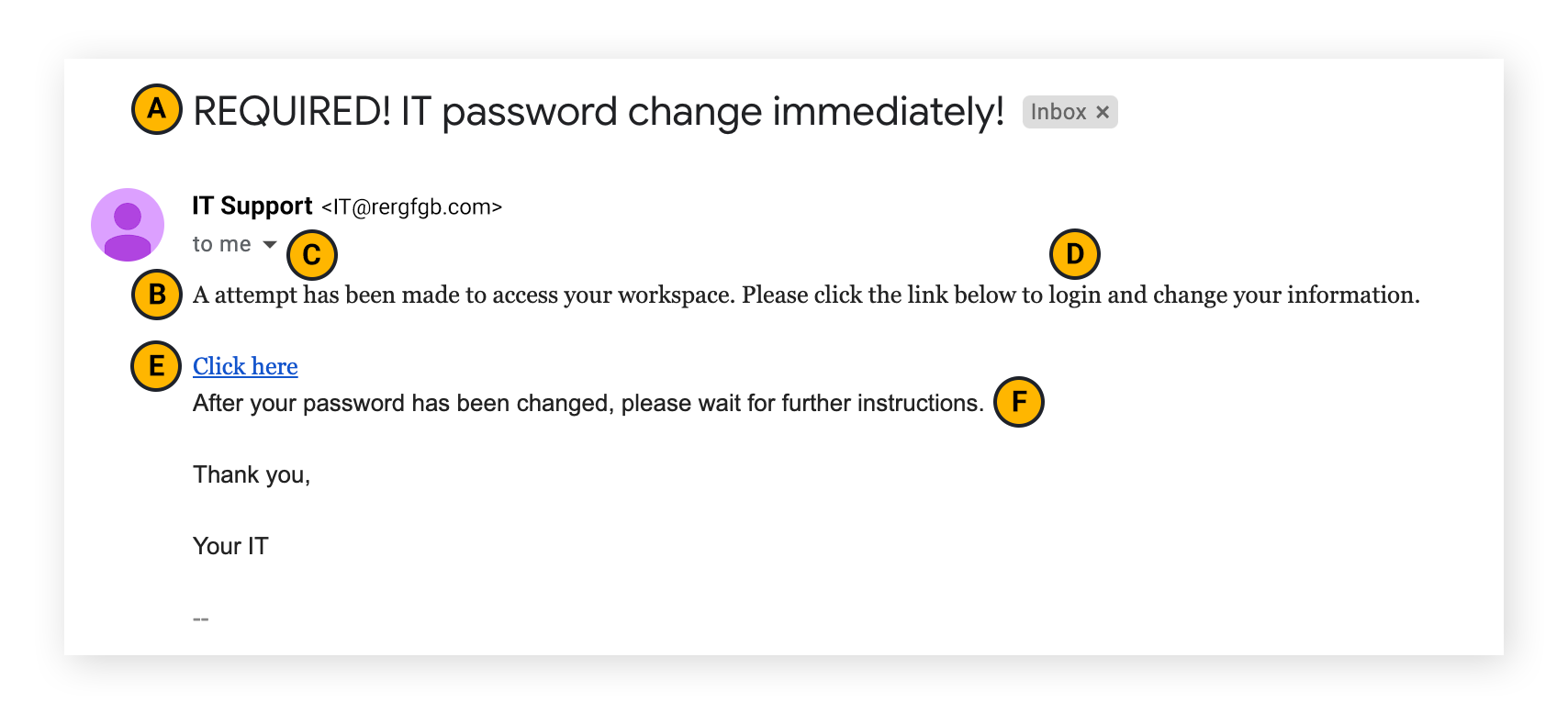 Some tell-tale signs of a spear phishing email: (a) unusual urgency or an unprofessional tone in the subject line; (b) typos; (c) a generic greeting or no greeting; (d) small grammatical errors; (e) lack of clarity about links; (f) strange spacing or mismatched fonts.
Some tell-tale signs of a spear phishing email: (a) unusual urgency or an unprofessional tone in the subject line; (b) typos; (c) a generic greeting or no greeting; (d) small grammatical errors; (e) lack of clarity about links; (f) strange spacing or mismatched fonts.
For added security against spear phishing attacks, check the email address carefully. If a name is misspelled or an unusual domain is used, it could indicate a fraudulent email. The attachment may also have an unusual or nonsensical name. If the message appears to be from someone you know or from an official source, but includes strange or unusual requests, contact the person directly to confirm the email is legit.
You should also follow basic internet and email security protocols, such as avoiding suspicious links, creating strong passwords, using secure and private browsers, and keeping your software updated. And make sure to back up your data so you don’t lose it in case your account is ever compromised.
Additionally, using security software will reinforce the anti-phishing capabilities of your preferred email client. The best antivirus software can help prevent you from becoming the victim of a spear phishing attack.
Protect against spear phishing attacks with AVG Antivirus
AVG AntiVirus Free has six layers of security that protect your data and keep would-be attackers away. And it features a built-in web shield that warns you of suspicious websites and an email shield that blocks dangerous emails and suspicious links.
Malicious attacks go beyond phishing — hackers use various types of malware, such as spyware or ransomware, to corrupt your device and steal your data. As online threats proliferate, prevention and security are more important than ever. AVG AntiVirus Free keeps you protected 24/7 against the variety of online threats out there today.
AVG AntiVirus FREE safeguards your device to ensure you don’t become a victim of spear phishing or other online attacks. Turn your device into a fortress and make sure your personal documents and data stay safe. Get AVG’s industry-leading protection today — completely free.




 Some tell-tale signs of a spear phishing email: (a) unusual urgency or an unprofessional tone in the subject line; (b) typos; (c) a generic greeting or no greeting; (d) small grammatical errors; (e) lack of clarity about links; (f) strange spacing or mismatched fonts.
Some tell-tale signs of a spear phishing email: (a) unusual urgency or an unprofessional tone in the subject line; (b) typos; (c) a generic greeting or no greeting; (d) small grammatical errors; (e) lack of clarity about links; (f) strange spacing or mismatched fonts.




