What is hacking?
Hacking means compromising computer systems, personal accounts, computer networks, or digital devices. But it’s not necessarily a malicious act — there’s nothing intrinsically criminal baked into the official hacking definition. Another way to define hacking is simply as the use of technology or related knowledge to successfully bypass a challenge.
So what is a hacker? Based on how we’ve defined hacking here, a hacker is someone who leverages their technical skills and knowledge to solve a problem or challenge. Again, there’s nothing inherently bad about it.
When hackers breach a computer network or system, that’s called security hacking. And though the media typically depicts hackers as cybercriminals who thrive on stealing data and wreaking all sorts of other digital havoc, that type of illegal hacking is properly termed cracking.
A brief history of hacking activity
The first people to apply the term hacking in a technological context were the members of MIT’s Tech Model Railroad Club. After the Second World War, these students started to use hacking to describe creating an innovative solution to a technical challenge. As computers emerged in the 1960s, curious club members took the term with them as they entered a new technological space.
A hacker is someone who leverages their technical skills and knowledge to solve a problem or challenge.
But it wasn’t until the 1980s that hacking exploded. For the first time, computers were available to the general public, and at affordable prices — almost anyone could buy a computer and experiment with hacking.
And experiment they did: Criminal hacking became so prevalent that in 1986, the US passed the Computer Fraud and Abuse Act, the world’s first anti-cybercrime law. Many of the world’s most dangerous hackers in recent years take their cues from those early pioneers.
Types of hackers
At its core, hacking is about unbridled creativity, fearless innovation, and the boldness needed to push past standard modes of thought. But not all hackers are satisfied with hacking for its own sake.
The hacking community can be divided into three broad groups, based on the legality of what they’re doing.
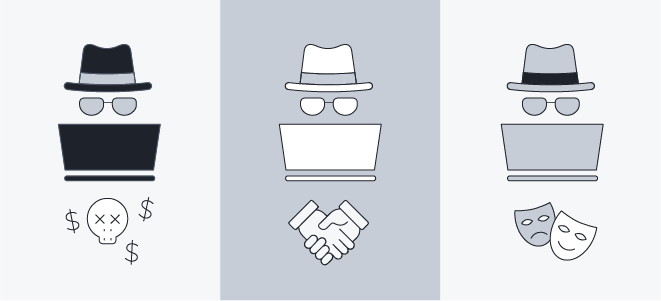 The three types of hackers: black hat, white hat, and grey hat.
The three types of hackers: black hat, white hat, and grey hat.
Black hat hackers
Black hat hackers are the kind the media loves to portray — the cloaked cybercriminal nimbly breaching a computer system to steal data, alter records, or pursue other unlawful aims.
If a black hat hacker discovers a vulnerability in a piece of software, they’ll take advantage of the flaw for criminal ends. They may create an exploit — a software tool used to leverage a given vulnerability — to get inside a computer system to spread malware. Or, they might sell their discovery on the dark web.
Sometimes, black hat hackers will even try to coerce (or bribe) people to do the hacking for them in what’s known as an insider threat. In August 2020, a hacker offered a Tesla employee $1 million to covertly install ransomware at the company’s Gigafactory in Nevada, USA. But, fortunately, the employee reported the offer to the FBI instead, and the hacker was arrested.
White hat and ethical hackers
In contrast to their black-hatted brethren, white hat hackers do all their hacking out in the open. In fact, white hat hackers are the opposite of their black hat counterparts. Companies will often hire white hat hackers to deliberately hack their systems and software to identify any vulnerabilities or security flaws — a technique known as penetration testing. That way, companies can strengthen their security before a black hat hacker can break through. That’s why white hat hackers are said to practice ethical hacking.
Some white hat hackers work in-house at large organizations, whereas others are freelancers or contractors. In addition to security hacking, ethical hackers can target employees with phishing campaigns to test an organization’s resistance to real-world attacks and help to identify areas in which additional cybersecurity training may be needed.
Grey hat hackers
Grey hat hackers exist in the nebulous boundary between white and black. They’re not explicit altruists, like white hat hackers, nor are they singularly focused on criminal activities. Grey hat hackers tend to hack first and ask for permission later, unlike ethical hackers who get consent in advance.
Many grey hat hackers start by probing a company’s systems or software to identify a security flaw. Only then do they reach out to provide a solution — for a fee, of course. Others use hacking as a tool for activism, publicly exposing vulnerabilities so that the targeted company has no choice but to fix them. In 2013, a grey hat hacker confronted Mark Zuckerberg directly using the security bug the hacker discovered to post on the CEO’s private wall, after Facebook had repeatedly rebuffed his previous attempts to report it.
While grey hat hacking may result in positive outcomes, it’s nevertheless illegal to practice security hacking without prior consent.
Is hacking illegal?
In and of itself, hacking is fine. But when you hack without getting prior consent, it crosses the line from legal hobby to illegal cybercrime. That’s why what white hat hackers do is fine — their employers and clients have given them permission to hack — and it’s also why grey hat hackers can face legal repercussions if they come forward with their findings.
In and of itself, hacking is fine. But when you hack without getting prior consent, it crosses the line from legal hobby to illegal cybercrime.
And, of course, all black hat hacking is illegal. If you’re on the receiving end of some black hat hacking, you can and should report the cybercrime to your country’s or region’s relevant authorities. That can potentially reduce the harm done, help bring the hacker to justice, and prevent others from being victimized in the future.
Common techniques used in hacking
Now that we’ve covered what hackers do, how do they do it? Depending on what the hacker is after, and who they’re targeting, they’ve got a wide range of hacking techniques at their disposal. Let’s dive into the various types of computer hacking by taking a closer look at several of the most common hacking examples.
Phishing
Phishing is a sneaky kind of cyber attack in which a cybercriminal attempts to fool their targets into divulging sensitive personal information like passwords or credit card details. The attacker can then use that information to hack into a victim’s accounts and commit fraud or theft, often by making purchases or applying for loans using the victim’s information.
Many phishing attacks are conducted via email. The phisher will send an email that mimics an official communication from a trusted party, such as a bank, hoping that the victim will fall for the ruse and reply with the requested information. Other attackers will phish with SMS messages (smishing), phone calls (vishing), or through social media platforms.
DNS spoofing
DNS spoofing is a technique that tricks your browser into sending your internet traffic to the wrong place. Websites and web servers have two ways of identifying themselves online. The first is the domain name, which is what you enter into the address bar of your browser (ours is avg.com). The second is the IP address, which is a string of numbers that helps any device on the internet identify any other device it’s communicating with (check out our guide to finding your IP address).
While people use domain names, computers use IP addresses. The DNS, or domain name system, links the two together. It’s like a phone book with all the names and numbers of anyone you’d ever need to call, except it’s for websites. DNS spoofing, also known as DNS cache poisoning, is when a hacker alters the DNS information so that a domain name points to a different IP address from the one it should — toward a malicious website controlled by the hacker.
Sometimes, your browser will request the DNS information from a dedicated DNS server, and some DNS spoofing attacks target those servers. But if you’re visiting a site you’ve been to before, your browser has the DNS information stored locally in a cache. So, other DNS attacks will manipulate, or poison, the DNS cache on your computer, usually via malware.
Either way, the result is that your browser leads you away from the actual website you want to visit and instead takes you to the hacker’s site. DNS spoofing is a popular setup for a pharming attack, where a hacker creates an imitation of a trusted website to trick you into “logging in” with your username and password. Once you do, the hacker has your credentials. Pharming and phishing attacks are both frequent precursors to identity theft and identity fraud.
Cookie theft
Also known as session hijacking, cookie theft happens when a hacker captures session data and uses it to impersonate you on a website that you use. Cookies are tiny little files that websites store in your browser so that they can remember your settings, behavior, and preferences. And a session is an exchange of data between you and a web server, from the time you begin using a site until you leave it or close your browser.
Some cookies are helpful — they remember your username and password, or your location, or which items you’ve placed in your shopping cart. Some websites use cookies that can log your actions: what you click on and when, or which search terms you use. And third-party tracking cookies follow you around the internet — monitoring the digital trail you leave behind online — then report back to advertisers so they can target you with ads they think you’re more likely to click.
If you’re browsing on an unsecured Wi-Fi network, a hacker can intercept the cookie that identifies you to the website you’re using. Then, the hacker can send that cookie back to the website to impersonate you and take actions on your behalf — such as logging into your bank account and helping themselves to your funds.
Cross-site scripting
Cross-site scripting (XSS) is a type of website attack in which a hacker injects, or adds, their own code into a legitimate website. That then causes the website to behave differently, typically with adverse effects on other users.
Many hackers use XSS attacks to hijack a victim’s session cookies in a cookie theft attack (as described in the section above). Other hackers will use XSS to turn legitimate websites into phishing portals that can log and capture all the data you enter while there — such as your username and password.
Because these attacks happen to a website, and not to you directly, it’s the website administrator’s job to prevent cross-site scripting. In the hands of a skilled hacker, many XSS attacks are impossible to detect by those who visit an infected website.
SQL injection
SQL injection (SQLI) is another type of attack in which a hacker injects their own code into a website. But instead of modifying the way a website works, SQL injection attacks target the database stored on a website’s server. The aim is to copy, alter, delete, or otherwise modify the database.
For example, a hacker may breach a website’s database with SQL injection and cause the database to export a list of user information, which the hacker can then use to commit identity theft. Or, they may simply delete large amounts of data, resulting in massive financial damages and chaos for the targeted company.
As with cross-site scripting, preventing SQL injection attacks largely falls to website developers and database administrators. It’s their responsibility to make sure their websites don’t have vulnerabilities that hackers can exploit with SQLI.
Protect yourself against data breaches
Many of the types of hacking described above can lead to massive data breaches, especially when hackers target large companies that keep piles of data on millions of people. The Equifax data breach of 2017 compromised the records of almost 150 million US citizens, as well as more than 15 million British citizens and many Canadians as well.
Hackers got in by exploiting a known software vulnerability that Equifax hadn’t patched on their own servers, even though a security update for the flaw had already been made available. Once inside, the hackers spent more than two months gradually harvesting data on millions of people.
The first step to protecting yourself against data breaches is to make sure you have a strong, unique password for each of your online accounts.
For a second line of defense, consider using a breach-monitoring service. AVG BreachGuard can protect you if and when a website you use suffers a breach. If your data is being exploited and sold on the dark web, BreachGuard will alert you so that you know which service suffered the breach and whether you’ve ever used the compromised password for any other accounts. That way, you’ll be able to protect yourself and prevent future leaks.
What types of devices can be hacked?
We’ve all heard plenty of stories about computer hackers, but the world of hacking involves a lot more than just your trusty computer. Nearly any digital device can be hacked, including phones, tablets, and all kinds of smart devices — but it can take time.
And it’s the time factor that usually determines whether a given device is vulnerable to hacking. Anyone attempting to hack your personal devices is likely in it for financial gain, and it’s simply not worth their effort if it’s going to take multiple years or more.
 Almost any digital device can be hacked.
Almost any digital device can be hacked.
But not all devices have the same protection against hacking. While Apple’s iOS is famously resistant (but not immune) to hacking, Android users can find themselves at risk if they install loads of sketchy apps from third-party developers. If you jailbreak your phone — hacking it yourself to remove built-in security protections and unlock capabilities — you’re leaving yourself wide open to hacking, especially if you don’t know exactly what you’re doing. The last thing you want is to find yourself having to remove malware from your phone.
Outside of computers and phones, cybersecurity protections can get a lot weaker. For example, many people — maybe you, but hopefully not — never change the default admin password on their router. Hackers know these passwords, and they can (and do) try them on people’s Wi-Fi networks. A hacker with access to your router can redirect your internet traffic, steal your personal data, install malware on your devices, and even access illegal content under your name. You can prevent router hacking by setting strong admin and network passwords and, if possible, by disabling WPS (Wi-Fi Protected Setup) on your router.
Smart devices also tend to be more vulnerable to hacking than computers and phones. And if a hacker infiltrates one of your smart devices, they may be able to access your entire home network. Protect your smart home by avoiding extra-risky smart devices, and wipe your data from any smart device before getting rid of it.
How will I know if I've been a victim of hacking?
Wondering if you’ve been hacked? While some of the warning signs of hacking are immediately obvious, others — like the long-term consequences of identity theft — can take a while to reveal themselves. By that point, it might be too late to avoid the damage.
Take an active stand against hackers by securing your accounts with AVG BreachGuard. You’ll get 24/7 surveillance on all your accounts so that you’ll be the first to know if any of the websites and services you use suffer a data breach, and if any if your personal data is at risk. Plus, BreachGuard’s specialized privacy guidance will help you adjust your settings and create robust passwords so you’ll be more protected against hacking than ever before.
Hacking warning signs
If you’ve been a victim of hacking, here are some warning signs:
-
Your computer or phone starts acting strangely. A series of unexpected changes to your computer or phone may point to a hacker. Look for passwords that no longer work, settings that have changed, and the presence of new files or programs that you don’t remember adding yourself. If your camera and microphone are activating when they shouldn’t, that can be a strong sign that your phone has been hacked.
-
Your antivirus software is deactivated. This is a big red flag, as your antivirus software’s sole job is to keep you safe. If it’s been deactivated without you doing so, that may point to hacking.
-
Your internet traffic is being redirected. Hackers inside your browser or your router can redirect your internet traffic to malicious websites. They may also change your default search engine to one that fills your browser with ads.
-
Someone’s spending your money. One of the most common motivations behind identity theft is monetary theft. Check your accounts regularly and be on the lookout for any unrecognized expenses or other questionable activity.
-
Your passwords don’t work. When a hacker gains access to one of your accounts, a common first step is to lock you out by changing your password. If you can, reset your password, activate two-factor authentication (2FA) if possible, and then alert the website or service about the incident.
-
You’re seeing way more ads and pop-ups than usual. Hackers love showering you with ads, because they earn money for each ad you see. Whether it’s a case of adware or a bit of trickery with your internet traffic, an uptick in ad frequency and quantity may indicate hacking.
-
The hacker reaches out. This one is, to put it lightly, hard to miss. Hackers who use ransomware will make sure you know that they’ve locked up your files, because they’re demanding a payment to release them. And a hacker threatening to dox you will likely demand payment in exchange for keeping your information secret. If anything like this happens to you, immediately notify your local authorities.
-
Your friends reach out. A hacker inside your social media accounts can scam all your contacts by pretending to be you. Your friends and family may contact you to ask what’s going on, and why you’ve been sending them all sorts of strange links.
Tips for defending against the hackers
When it comes to keeping hackers out, a little daily digital hygiene can go a long way. So long as your devices and accounts are harder to hack than the next person’s, the typical hacker will move on to greener (easier) pastures.
It’s like escaping from a bear: you just need to run faster than the person next to you.
 Keep your software current. Hackers can exploit vulnerabilities in outdated software to breach your device. Always install software updates, and use auto-update whenever it’s available.
Keep your software current. Hackers can exploit vulnerabilities in outdated software to breach your device. Always install software updates, and use auto-update whenever it’s available.
 Use strong and unique passwords on all your accounts. This ensures that a hacker who knows one of your passwords won’t be able to get into any of your other accounts. The same can’t be said if you reuse your passwords.
Use strong and unique passwords on all your accounts. This ensures that a hacker who knows one of your passwords won’t be able to get into any of your other accounts. The same can’t be said if you reuse your passwords.
 Click with caution. Sometimes hackers infect websites with malicious ads and links, which when clicked can download malware to your device. These can’t hurt you if you avoid them.
Click with caution. Sometimes hackers infect websites with malicious ads and links, which when clicked can download malware to your device. These can’t hurt you if you avoid them.
 Avoid websites without HTTPS encryption.
Avoid websites without HTTPS encryption.
When you see a URL that begins with HTTPS, or if you see a little padlock icon in your browser’s address bar (as you will right now), it means that the website you’re on is protecting your data with encryption. Don’t enter any personal information into websites that lack HTTPS encryption.
 Set your own usernames and passwords on your router and smart devices. Hackers know the default passwords for many routers and other smart devices. Set new passwords as soon as you get an additional device, whether it’s new or secondhand. And make your Wi-Fi network name (SSID) and password both long and complex.
Set your own usernames and passwords on your router and smart devices. Hackers know the default passwords for many routers and other smart devices. Set new passwords as soon as you get an additional device, whether it’s new or secondhand. And make your Wi-Fi network name (SSID) and password both long and complex.
 Install an antivirus program. AVG AntiVirus FREE is a robust and reliable cybersecurity solution that detects and blocks malware and other hacking tricks before they have a chance to affect your devices. And the dedicated Network Inspector feature will keep Wi-Fi hackers out of your network.
Install an antivirus program. AVG AntiVirus FREE is a robust and reliable cybersecurity solution that detects and blocks malware and other hacking tricks before they have a chance to affect your devices. And the dedicated Network Inspector feature will keep Wi-Fi hackers out of your network.
Long-term tips to prevent hacking
After you’ve implemented the quick fixes described above, be sure to follow the tips below to protect yourself against hacking in the long term. Make these part of your digital lifestyle ASAP.
-
Be careful on public Wi-Fi and public computers. When using an unsecured public Wi-Fi network for anything more significant than a quick internet search, protect your traffic with a VPN. And never log into your personal accounts on a public computer — a hacker may have previously installed spyware on it.
-
Use a VPN. A VPN encrypts all the internet traffic coming to and from your device. Try AVG Secure VPN to secure your connection on unsecured public Wi-Fi, and anywhere else for that matter. A VPN also hides your identity while you’re online, preventing anyone from seeing what you’re doing.
-
Use a password manager. If you’re following our earlier advice and creating unique passwords for all your accounts, a secure password manager will keep them all in one place.
-
...and don’t store passwords in your browser. This is not a secure way to store all your complex new passwords. Instead, look for a password manager that you can install as a browser extension, maybe even with an auto-fill feature.
-
Use two-factor authentication (2FA) wherever you can. While it’s not completely hack-proof, using 2FA is more secure than not using it. If a website or service offers 2FA, use it. There’s no downside, save for a few seconds of minor inconvenience.
-
Learn how to detect phishing and pharming attacks. AVG AntiVirus FREE protects you against phishing and pharming, but it’s still good to know the fundamentals. A healthy dose of skepticism can serve you well on the internet.
-
Download programs and apps from official sources. When downloading apps, do so from the developer’s own website — or, if you’re on mobile, from Google Play or the Apple App Store. When installing new apps, check to see if there’s any additional (and unnecessary) software bundled in. If so, you should be able to avoid downloading the bloatware.
-
Pay close attention to app permission requests. Yes, actually read them. Apps shouldn’t ask for more permissions than they need. Be especially skeptical of apps that want to access your contacts, location data, microphone, and webcam.
Use an antivirus to protect yourself from hacking
All the personal vigilance in the world won’t save you in the event of a large-scale data breach. But with AVG AntiVirus FREE, you’ll stay ahead of hackers with a powerful cybersecurity solution that scans for and blocks malware and other nasty tricks hackers use to infect your device. It’ll protect you from unsafe links, risky downloads, shady email attachments, and more. Download AVG AntiVirus FREE right now and lock hackers out before they ever have a chance to get in.

 The three types of hackers: black hat, white hat, and grey hat.
The three types of hackers: black hat, white hat, and grey hat.




