What is a strong password?
A strong password is one that’s difficult for someone to guess or a program to hack. Password strength is a measure of how long or how many attempts it would take for an attacker who doesn’t have access to the password to guess it correctly.
Long, complex passwords or passphrases that mix groups of words together are very strong. Short, generic, and easy-to-remember passwords are weak, because they can be easy to guess or vulnerable to brute-force attacks.
Making your password longer and more complex increases the number of attempts an attacker would need to successfully crack it — with sufficient complexity you can make your password essentially uncrackable. There’s no clear threshold for how long passwords should be to be considered “strong.” In general, longer and more complex passwords are stronger and better.
What makes a password strong?
The best, most powerful and strongest passwords are long, hard-to-guess, and unique. That means using a minimum of 15 characters, using words or phrases that are hard to guess and difficult to connect to you, and never reusing passwords across multiple accounts. Good password ideas satisfy all three of those requirements.
Complexity is often used as a key criterion of a secure password — meaning that you should use a mixture of uppercase and lowercase letters as well as numbers and symbols. While this is true, password length is more important than complexity, which is why passphrases often make the best passwords. It’s easier for a shrewd hacker to crack a short, complex password than a longer one, even if it’s composed of only lowercase letters.
Strong password examples
Here’s a look a few good password ideas:
Each of the above examples is long and randomized with no discernable pattern, and they are considered very strong passwords. The complex ones combine a mixture of numbers, upper and lowercase letters, and special characters. The passphrases combine words or sayings into a random mix.
How to create strong and unique passwords
Generating good passwords that fit all the criteria can seem daunting, especially since it’s so important to create unique passwords for all your accounts. If you need tips for strong password creation, there are several approaches you can take. And password manager tools are great options to create and store all your different passwords.
Use a password manager
Many of the best password managers will automatically generate new passwords for you. Since your password manager securely stores all your passwords and other login credentials, you can let it create unique passwords that are as long and complex as you like. The longer the suggested strong password is, the harder it’ll be to crack.
Here’s how to make a good password with BitWarden, a free password manager. The process should be similar with whichever password manager you choose.
-
Download BitWarden and set up your account.
-
Click the BitWarden extension icon in your browser to open the menu, then click Generator.
-
Adjust the settings to your needs and your password manager will automatically create a strong password for you.
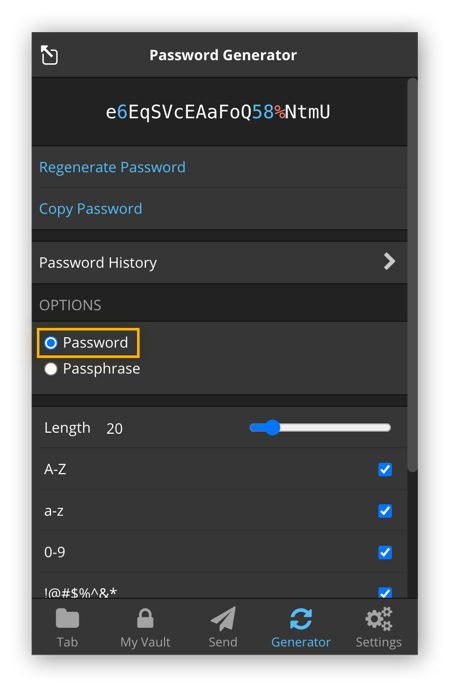
The ability to create strong passwords and store them securely is the primary reason why you should use a password manager. If you do, you’ll only need to remember one password: the master password that you use to log into your password manager.
Play with your keyboard for unique ideas
Getting creative with your keyboard can help you memorize long strings of randomized letters, numbers, and other characters that you’d otherwise struggle to remember. Look for letters or shapes hidden in patterns on your keyboard, and use special characters in the form of “emoticons.”
For example, by starting in the far bottom-left corner with the Z key and tracing the letter M across your keyboard, you end up with zsefvgyjm. Then, you can strengthen it by adding emoticon special characters and capitalizations to give you the seemingly meaningless password :/ZsefvgyjM!:).
 Keyboard pattern character strings are memorable to you and difficult for others to guess.
Keyboard pattern character strings are memorable to you and difficult for others to guess.
Customize your password with common elements
Although you should never reuse identical or very similar passwords, you can use common elements within your passwords. To take the above example, you may use :/ZsefvgyjM!:) as the common element — the base upon which you will construct other, longer and more secure passwords — for each of your accounts, like so:
-
Banking password: $_:/ZsefvgyjM!:)_BohRdA
-
Facebook password: #_:/ZsefvgyjM!:)_FbuwBK
-
Steam password: 8)_:/ZsefvgyjM!:)_StOPqM
Use a passphrase
Using a passphrase helps you make a strong password that’s also easy to remember. A passphrase is a string of words that’s much easier to remember than complex combinations of upper and lowercase letters, numbers, and special characters. Due to their length, well constructed passphrases can be exceptionally difficult to crack. Just make sure that the words are not closely related to one another.
What is a passphrase?
A passphrase is a string of unrelated words that you use as a password. Because they’re made of words, passphrases are often easier to remember than conventional, complex passwords with many different types of characters. It’s the length of a good passphrase, as well as the randomness of the words in it, that makes it secure.
We’re not alone in loving passphrases — in a May 2021 article, the FBI stressed the importance of using “passphrases that combine multiple words and are longer than 15 characters.”
The image below is a great starting point for coming up with your own passphrases. SunnyBroomAirplaneHorseGraduation would be nearly impossible for anyone to guess, and even harder for a hacker to crack.
 The best passphrases are composed of completely random words.
The best passphrases are composed of completely random words.
Passphrase vs password
Whereas passwords are a single set of mixed characters, passphrases are made up of multiple words that form a longer string of text. Because password length is paramount when it comes to defeating the cracking techniques hackers use, passphrases are not only easier to memorize. They’re also more secure than shorter, more complex passwords.
How to create good passphrases
The key to a good passphrase is randomness — the words you use to create a passphrase should not have an obvious connection between them. A good passphrase example is overripe-trekker-angular-envision-letter, while a passphrase like apple-peach-banana-cucumber would be much easier to crack.
You can separate the words with hyphens, spaces, periods, by capitalizing the first letter of each, with a number, etc. All of those choices are great for creating a strong passphrase.
Create good passphrases with a password manager
Many password managers can be configured to create good passphrases that meet the criteria of the best passwords. Let’s look at how to create passphrases with a password manager.
-
Open your password manager’s browser extension and find the password generation feature. (Here, we’re using the BitWarden password manager again.)
-
Select the option for passphrase creation and configure the settings as needed.
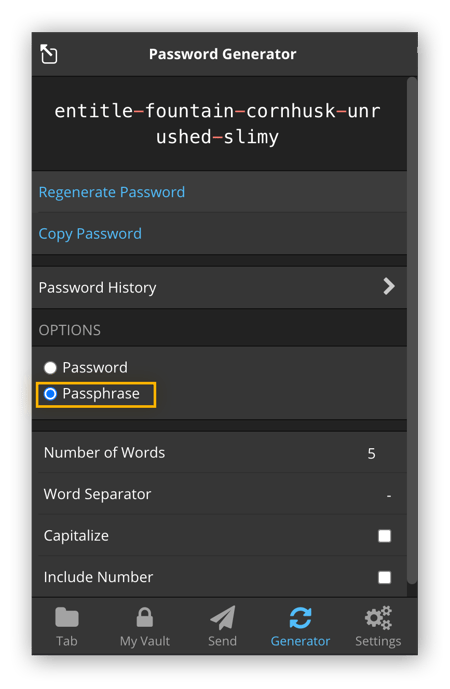
-
Generate new passphrases until you get something you can remember, adjusting the settings if necessary.
Create good passphrases with a passphrase generator
If you don’t want to use a password manager, there are plenty of websites that will generate good passphrase ideas for you. Use a Passphrase is a passphrase generator that also tells you approximately how long it’d take a hacker to crack your new passphrase.
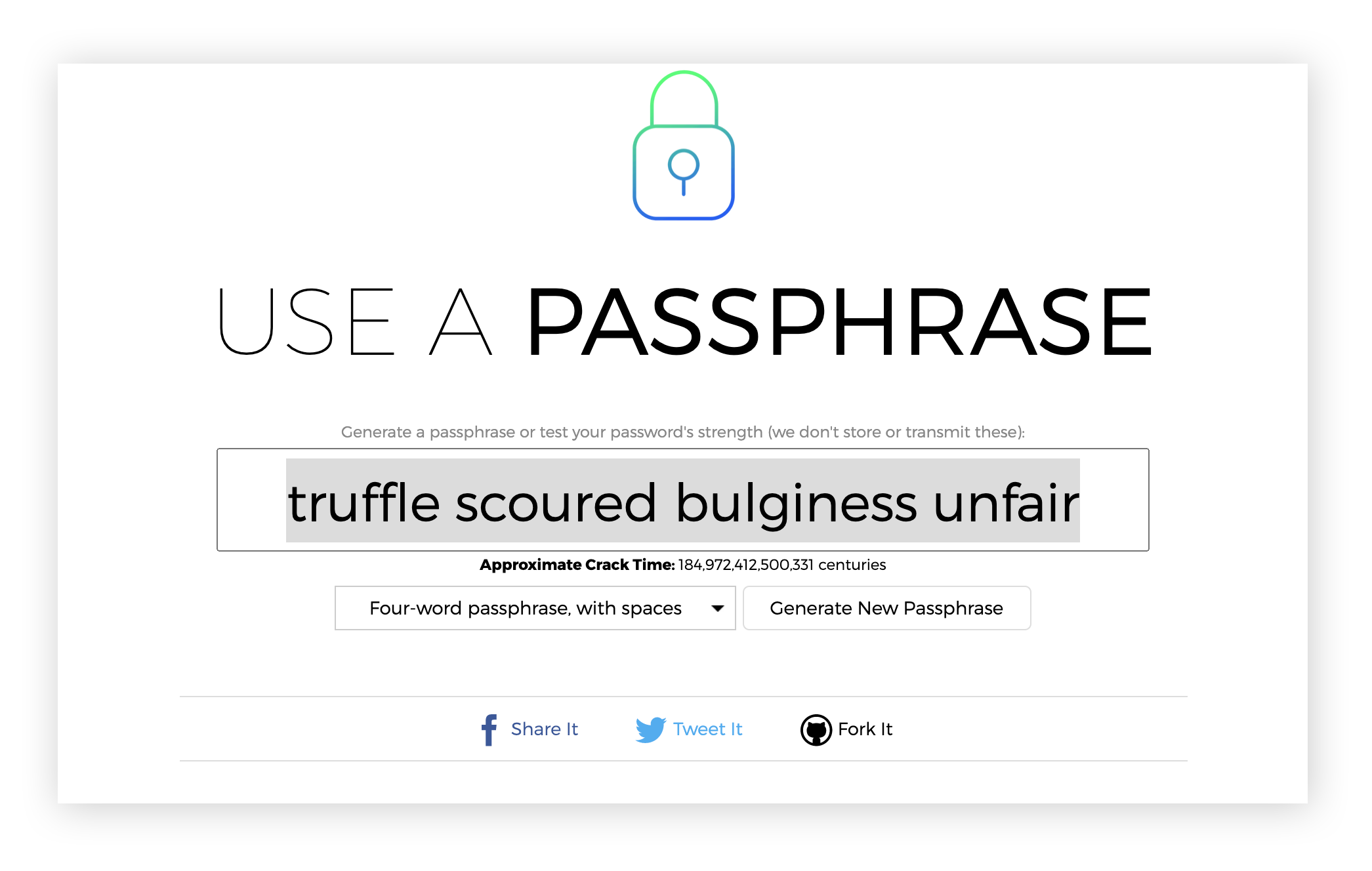
Even the most dangerous hackers of today will struggle to crack a passphrase that’s projected to take hundreds of trillions of centuries to unlock. Just pick your desired passphrase configuration from the options, and you’re good to go.
Good passphrase examples & passphrase ideas
Good passphrases are easy for you to remember and hard for hackers to guess. And since passphrases are long, they’re practically impossible for hackers to crack via brute-force attacks.
Here are a few good passphrase ideas created with BitWarden:
-
console-shrubbery-bronchial-various-squatter
-
Broadways&Swimmer&Argue7&Pursuant&Dramatize
-
Rickety Output Oxidant Deem Spotless
-
unguarded3 superglue evacuee paddling gloomy shuffling
-
seclusion.roast.chop.unrated9.quarrel.morbidly.planner
The length of these passphrases, plus their randomness, makes them strong password examples.
How to remember a passphrase
The best way to remember your passphrase is to create a story that ties all the words together. This story can be as simple or as complex as you like — so long as you can remember it.
Let’s consider the first passphrase in the previous section:
console-shrubbery-bronchial-various-squatter
The story here might be that, while playing my video game console, I noticed the shrubbery outside was causing bronchial distress for the various squatters living nearby. If I need to remember my passphrase, I can just look at my video game console, and the rest of the story will fall into place.
Since they’re easy to remember, passphrases are great for password-protecting files and devices in addition to your online accounts.
Once you’ve created new and highly secure passwords and passphrases, secure them against leaks and data breaches with AVG BreachGuard. You’ll be alerted immediately if any site you use suffers a data breach and leaks your login credentials. That way, you can change your passwords ASAP to keep hackers out of your accounts.
How to create a strong password: what not to do
Since the strongest passwords are long, hard to guess, and unique, most weak passwords are missing one of these crucial qualities. Many people leave themselves and their data open to hackers by using a simple word, repeating their passwords, or making other common password-creation mistakes.
Here’s what not to do when creating a new password:
-
Don’t repeat passwords. Using the same password across multiple accounts is convenient, but makes you very vulnerable to hacking. A hacker only needs to breach one of these accounts to get your login credentials for all the accounts using that password. Never use a password for more than one account.
-
Don’t use similar passwords. It’s not enough to change a password from teddybear1 to teddybear2. When creating new passwords or changing older ones, always use something completely new.
-
Don’t use personal info. If your passwords are based on personal info like your pet’s name, your job, or your hometown, a hacker can easily figure it out based on your social media presence and other information available online. People who know you personally might even try to crack one of your accounts this way.
-
Don’t use a short password. The days of eight-character passwords are over — these are way too easy to crack with modern computing. Your password shouldn’t be any shorter than 15 to 20 characters. Longer is always better.
-
Don’t use common character substitutions. Swapping in a 3 for an E may have worked back in the 1980s and 1990s, but these days, it’s best to leave 1337speak in the past. P455w0r|) is just as easy for a hacker to crack as password.
-
Don’t store passwords in plaintext. Plaintext is unencrypted text — like the text in this article. It might seem easy to store your passwords in a note or spreadsheet, but if that file falls into the wrong hands, all your accounts are compromised. If you want to store your passwords, use a password manager that securely encrypts your data.
How to keep a password secure
Secure passwords are an important first step, but even the strongest of passwords are useless if they fall into the wrong hands. That’s why storing your password safely is just as important as using a complex password that can’t be guessed or cracked.
After creating new passwords, here’s how to protect them:
Don't save your passwords on your phone or tablet
Don’t give in to the temptation to save your passwords on your phone or any other device — even within a password protected file or folder. If you do, you’re just one loss or theft away from having all your accounts compromised. Instead, store your passwords with a password manager that will keep track of all your logins for you, and protect your passwords against breaches and leaks.
Don’t share your passwords with anyone
Sending someone a password via email or text puts that password at risk of being intercepted, especially if you’re using an unsecured public Wi-Fi network. It’s somewhat safer to use a secure messaging app, but it’s safest to use a password manager that allows for secure password sharing between users.
Do not write your passwords down
No matter how strong your password is, if someone gets their hands on it, they’ve got control of your account. Writing down or otherwise insecurely storing a strong password is just as risky as using passwords that are easy to remember. Weak passwords and poor password-safety practices can result in hackers accessing your data, which they can then sell on the dark web or use to commit identity theft.
Do not reuse passwords
As tempting as it may be, you should never recycle passwords. When you use a password on multiple sites, it weakens that password for all those sites. As we’ve said throughout this piece — always keep your passwords unique.
Avoid malware
A malware infection can compromise your security by using keyloggers or other spyware techniques to record and steal your passwords. There’s no point using an uncrackable password if snoops can simply lurk on your system, watching every click you make and reading everything your type.
Always use a trusted malware and virus removal tool like AVG AntiVirus Free to keep threats at bay.
Secure your strong passwords with data breach monitoring software
While your new passwords are now strong and uncrackable, the websites you use them on may not be as secure. Websites are targeted by hackers for data breaches all the time, which can compromise thousands of user accounts.
If any of your passwords are caught in a breach, AVG BreachGuard will alert you immediately and aid you in changing your passwords to keep your accounts safe. Get AVG BreachGuard and start keeping your passwords secure today.



 Keyboard pattern character strings are memorable to you and difficult for others to guess.
Keyboard pattern character strings are memorable to you and difficult for others to guess. The best passphrases are composed of completely random words.
The best passphrases are composed of completely random words.







